JUCI Manual
Version 3.11
Introduction
Administration of the gateway is done through a web interface. All settings are accessible through an address on your local network.
Requirements
To access the web interface, you need the following:
An installed gateway device.
A computer connected to the LAN or WLAN port on the device.
A web browser installed on the computer.
The default address for the web interface is http://192.168.1.1.
Access web interface
To access the web interface you need to use your web browser. There are multiple ways of accessing the interface.
User Roles
The web interface uses Roles to provide and restrict access to the various features in the device.
There are four pre-defined roles: User, Support, Admin, and Root.
User Modes
In addition to User Roles, the User Modes may provide further constraints on what settings and features are displayed in the web interface.
Note: The mode affects display only, the features are still available and operational.
Features
Depending on your device and/or geographical region, certain features may be unavailable in the interface.
Applying changes
When you change a setting or a value in the interface, it gets added to a list of changes. The changes will not take effect until you click apply.
User Modes
In addition to User Roles, the User Modes may provide further constraints on what settings and features are displayed in the web interface.
Note: The mode affects display only, the features are still available and operational.
Basic Mode
Basic mode provides access to a selected set of settings and aspects of features, displaying a reduced set of options. This mode is suitable for the most common tasks and configurations.
Expert Mode
Expert mode provides access to a larger number of settings and aspects of features. This mode is suitable when you have deeper technical knowledge and want to do specific customizations or troubleshooting.
Basic Mode
Basic mode provides access to a selected set of settings and aspects of features, displaying a reduced set of options. This mode is suitable for the most common tasks and configurations.
Features
In basic mode, all Expert mode settings and views are hidden from the interface. However, if you select a particular task in basic mode that requires expert mode settings, they will automatically be displayed.
Expert Mode
Expert mode provides access to a larger number of settings and aspects of features. This mode is suitable when you have deeper technical knowledge and want to do specific customizations or troubleshooting.
Features
In expert mode, all Basic mode settings and views are also shown.
User Roles
The web interface uses Roles to provide and restrict access to the various features in the device.
There are four pre-defined roles: User, Support, Admin, and Root.
User
The User role has restricted access to basic set of features.
login: user
password: user
Support
The Support role has elevated access to basic and a set of advanced features.
login: support
password:support
Admin
The Admin role has unrestricted access to all basic and advanced features.
login: admin
password:admin
Root
The Root role has unrestricted to the device, and can be used for command line access to the device via ssh.
login: root
password:root
Features
Depending on your device and/or geographical region, certain features may be unavailable in the interface.
Availability
Certain features may not be available in your interface, depending on several factors:
Device - Your device may be limited in which ports are avaible.
Geographical region - Features might not be offered in some regions or countries.
Operator Settings - Your operator may have restricted, altered or added features in the software.
Applying changes
When you change a setting or a value in the interface, it gets added to a list of changes. The changes will not take effect until you click apply.
Access web interface
To access the web interface you need to use your web browser. There are multiple ways of accessing the interface.
IPv4
The standard IPv4 address for the interface is http://192.168.1.1.
Hostname
The web interface can be accessed through a default hostname, for example inteno.lan/ or routerlogin.net/, or through custom hostnames set up by the provider.
IPv6
An IPv6 address or IPv6 hostname can also be used to access the web gui.
* Launch your web browser * Enter the address (for example: http://192.168.1.1) * Press [Enter].
You are taken to the web interface login page.
Login
To login to the web interface, you use a user name and a password.
(For default passwords see: User Roles).
Note: Your operator may have specified different passwords and user levels. If so, you need to request those from your operator.
Log in to the web interface:
- Enter a user name
- Enter the password
- Click OK.
You are taken to the web interface Overview page.
Overview
The Overview page shows the most important statuses and settings for your device.
Parts
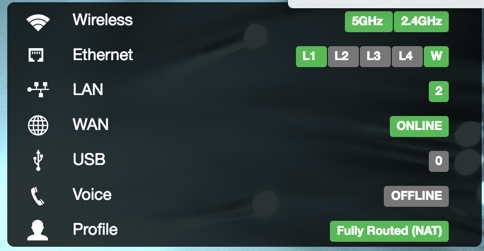
The overview has three parts: a device network map, configuration shortcuts, and status panels.
Device Network Map
The device map shows how your device is connected to the LAN and the WAN, as well as other devices in the local network.
Configuration Shortcuts
The configurations show status for and provide shortcuts provide quick access to various common settings.
Status Panels
The status panels display status information about selected features. They also allow you quick access to configuration of the most common features.
Device Network Map
The device map shows how your device is connected to the LAN and the WAN, as well as other devices in the local network.
View
Colors
The status of a device is indicated by the color of the icon.
| Color | Status |
|---|---|
| Green | Enabled and active |
| Black | Enabled, not active |
| Yellow | Active, with warnings. |
| Red | Active, not functional. |
Edit Node Settings
You can edit the settings for a node directly from the Device Network Map.
To edit a settings for a node:
- Click the node in the map
A window containing settings tabs opens.
Static Leases
The Static Leases tab allows you to assign a static IP address dhcp lease to the client.
Forwarding
Port Forwarding allows remote computers to connect to a specific device within your private network.
Details
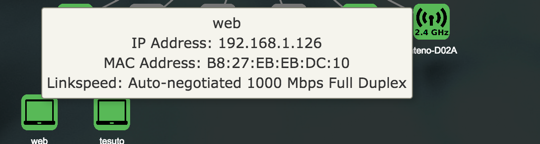
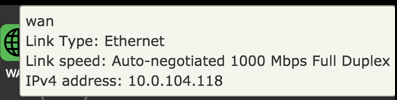
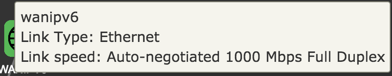
More detailed Information about the status of an item in the map is availabe by pointing the cursor at an icon in the map.
View
WAN
Device
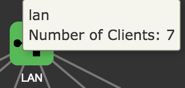
LAN
Port
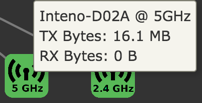
Wifi
Client
Configuration Shortcuts
The configurations show status for and provide shortcuts provide quick access to various common settings.
| Option | |
|---|---|
| Wireless | Active wireless radios. |
| Ethernet | LAN ports in use on the device. |
| LAN | Active LAN |
| WAN | Status of WAN connection. |
| USB | Connected USB devices, if any. |
| Voice | Voice port status, if any. |
| Profile | Selected network profile, if any. |
Status Panels
The status panels display status information about selected features. They also allow you quick access to configuration of the most common features.
WIFI
The WiFi status panel lets you change the default wireless security settings (WPS) to make your network more secure. You can also view the wifi status and edit the wireless interface.
LAN
WIFI
The WiFi status panel lets you change the default wireless security settings (WPS) to make your network more secure. You can also view the wifi status and edit the wireless interface.
WPS settings
WPS makes it easier to connect other wireless devices to your device on an encrypted channel.
Edit 5GHz Wireless Interface
In the edit wireless interface view you can change different aspects of your interface.
Edit 2.4GHz Wireless Interface
In the edit wireless interface view you can change different aspects of your interface.
WPS settings
WPS makes it easier to connect other wireless devices to your device on an encrypted channel.
Edit 2.4GHz Wireless Interface
In the edit wireless interface view you can change different aspects of your interface.
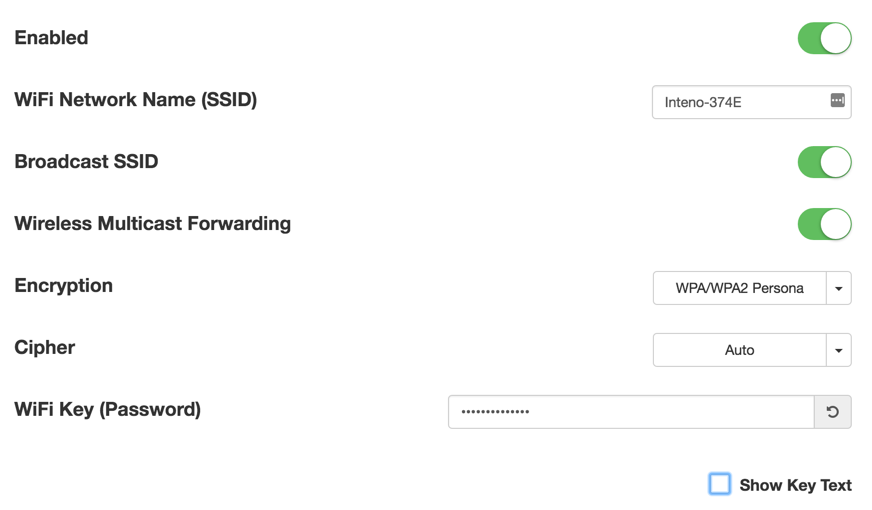
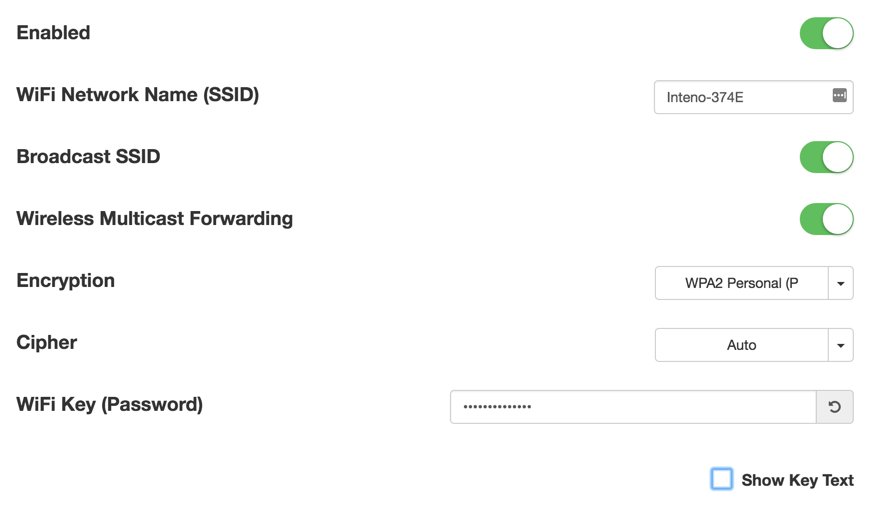
Wireless Settings
Edit 5GHz Wireless Interface
In the edit wireless interface view you can change different aspects of your interface.
| Item | Comment |
|---|---|
| Enabled | Toggle interface on or off. |
| WiFi Network Name | Edit name of SSID network. |
| Broadcast SSID | Toggle to make the network SSID visible or invisible. |
| Encryption | Selected encryption method. |
| Cipher | Form of Cipher. |
| WiFi Key (Password) | Text to use as wifi key. |
| Show Key Text | Displays the wifi key text. |
Wireless Settings
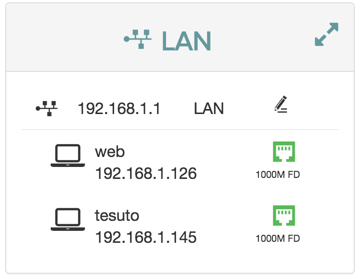
LAN
The LAN panel shows basic information about the device and connected clients IP addresses.
From the LAN status panel you can configure the DHCP settings for the device.
To open the Edit LAN Settings dialog, click the ![]() edit button.
edit button.
To view a more detailed overview of the clients, click the ![]() expand button
expand button
To view or details about a client click the client in the list.
Detailed Client Overview
In The Detailed Client Overview, information about the clients in the lan is displayed.
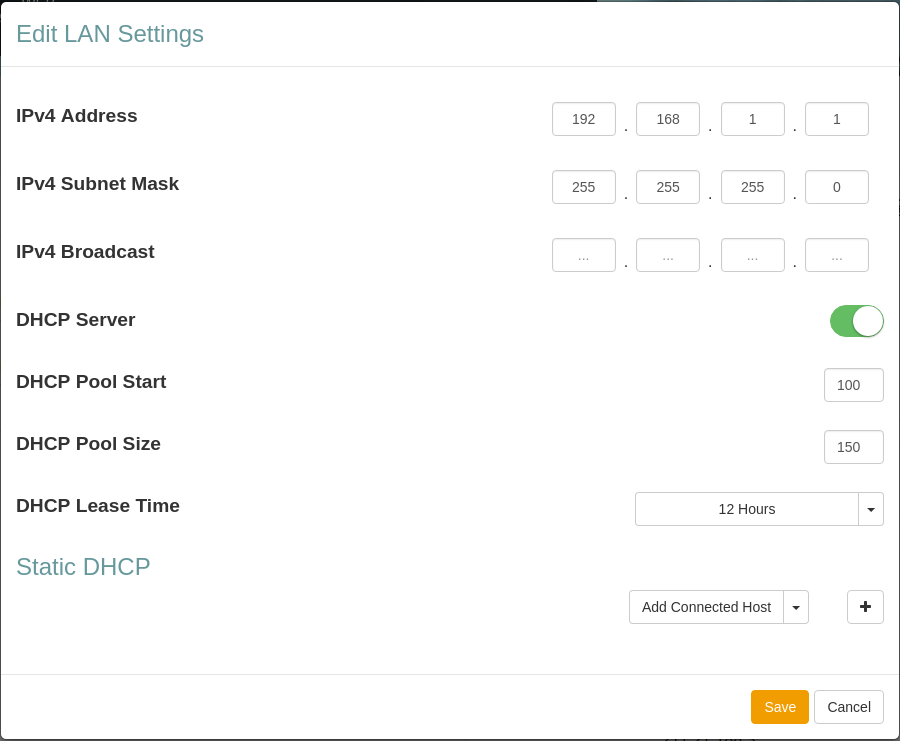
Edit LAN Settings
In The Edit LAN settings view you can change different features about your network.
Client
The Client dialog displays information about the connected clients and allows you to edit their configuration.
Detailed Client Overview
In The Detailed Client Overview, information about the clients in the lan is displayed.
| Item | Description |
|---|---|
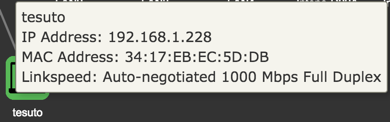
| Hostname | Client hostname. |
| IPv4 Address | Client IPv4 Address. |
| MAC Address | Client MAC Address . |
| Port | Device port. |
| Network | Network interface for the client. |
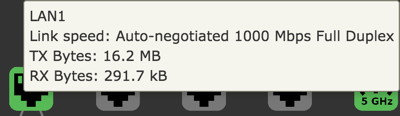
| Link Speed | Type of negotiation, speed and duplex for the connection. |
Edit LAN Settings
In The Edit LAN settings view you can change different features about your network.
| Item | Description |
|---|---|
| IPv4 Address | Device DHCP address |
| IPv4 Subnet Mask | IPv4 Subnet Mask |
| IPv4 Broadcast Mask | IPv4 Broadcast Mask |
| DHCP Server | Turn DHCP Server on or off. |
| DHCP Pool Start | Start IP number for the DHCP Pool start number IP address |
| DHCP Pool Size | Number of IP addresses in the DHCP Pool |
| DHCP Lease Time | DHCP Lease Time for the LAN. |
| Static DHCP | Reserve an IP address DHCP Lease for a connected device. |
Static DHCP
The Static DHCP section lets you configure IP address DHCP Leases for connected devices. |
Add Static DHCP Lease
To add a static DHCP lease:
- Add an existing client or create a lease from scratch:
- To select an existing client:
- Click Add connected host to open the list
- Select the desired client
- To add a static DHCP lease manually:
The information for existing client is added automatically, otherwise the fields will be empty.
- Add or edit the client information as neeed.
- Click Save
Client
The Client dialog displays information about the connected clients and allows you to edit their configuration.
Port Forwarding
In the Port Forwarding tab you can map incoming connections on different ports to ports on the client.
Static Leases
The Static Leases tab allows you to assign a static IP address dhcp lease to the client.
Realtime Graphs
For WiFi clients (it is not shown for regular lan clients), the Realtime Graphs tab you can map incoming connections on different ports to ports on the client.
Parental Control
Parental control is used to restrict access to the network for particular devices.
Internet Access Scheduling
Parental control is handled by setting schedules where access is restricted to explicitly named MAC addresses.
Add Parental Control
The Internet Access Schedule rules you add from the client panel will only apply to that client.
Internet Access Scheduling
Parental control is handled by setting schedules where access is restricted to explicitly named MAC addresses.
When adding a parental control filter from the client panel, the MAC Address is automatically selected from the client.
Add an Internet Access Schedule
- Select a Time Frame from the menu
- Edit the selected Days as needed
- Enter a time:
- From
- To
- Click Save
- Click Close
Start and Stop Times
The start time for a rule has to be lower than the end time.
If you want to have a rule that goes over midnight, you need to add two rules, one up until midnight, and one from midnight to when you want the rule to end.
For example:
Rule one: From 21:00 To 23:59
Rule two: From 00:00 To 06:00
A single rule of From 21:00 To 06:00 will not be saved.
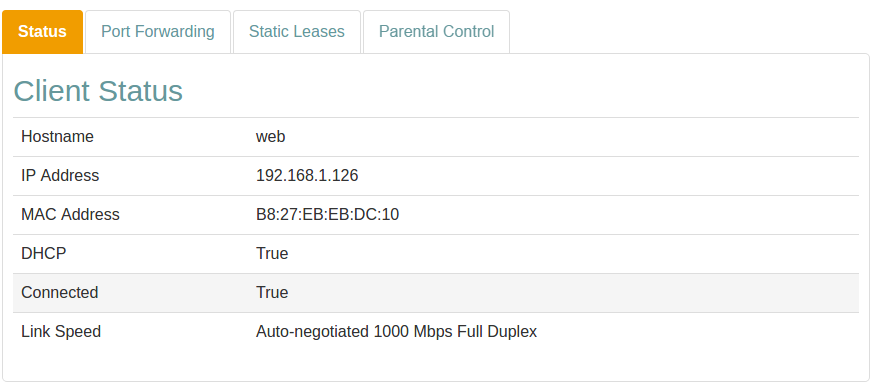
Status
The Status tab shows information about the client and the connection.
Status Information
Wireless Details
For WiFi clients, the Wireless Details section shows detailed information about the wireless connection. All data is measured since last downtime.
| Item | Description | Example |
|---|---|---|
| Frequency | WiFi frequency band for the access point. | 2.4GHz |
| RSSI | RSSI strength for the signal. | -64 dBm |
| SNR | Signal-To-Noise-Ratio. | 21 dBm |
| Idle | Time idle. | 1 s |
| In Network | Time in network. | 1813 s |
| WME | Status of WMM. | True |
| Power Save | Is Power save enabled? | False |
| N Mode | Is 802_11n supported? | True |
| VHT Mode | Is 802_11ac supported? | False |
| TX Bytes | Transmitted bytes. | 2438426 |
| RX Bytes | Transmitted bytes. | 347988 |
| TX Rate | Transmission rate. | 58 Mbps |
| RX Rate | Recieve rate. | 6 Mbps |
Port Forwarding
In the Port Forwarding tab you can map incoming connections on different ports to ports on the client.
Mapping Section
| Item | Description |
|---|---|
| Name | Port name. |
| Excluded ports | Protected ports that can't be mapped. |
| Public port | Public (external) port. |
| Private port | Private (client) port. |
| Protocol | Protocol. |
Protocol
The protocol setting filters traffic by protocol for the port forward.
Mapping Settings
To map incoming connections:
- Click Add mapping to open the mapping section
The mapping section lets you add configuration settings for the mapping.
Ports can be added one by one (80), as comma-separated lists (8080, 8090) or as ranges (21-22).
- Add information:
- Add a name as identification
- Add ports:
- Add public/incoming port(s)
- Add private/client port(s)
- Select protocol
- Click Save
- Click Close
Your information has now been saved and is visible in the mapping list.
Static Leases
The Static Leases tab allows you to assign a static IP address dhcp lease to the client.
Static Leases Section
Static Leases Settings
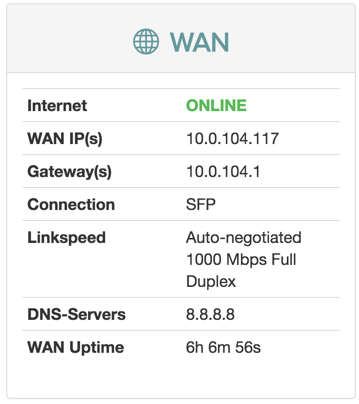
WAN
| Item | Description |
|---|---|
| Internet | Status of Internet connection. |
| Link | Status of link. |
| WAN IP(s) | IPv4 and IPv6 address to the device. |
| Gateway(s) | IPv4 and IPv6 address to gateway. |
| Link Type | Ethernet |
| Link Speed | Auto-negotiated 1000 Mbps Full Duplex |
| DNS-Servers | IPv4 and IPV6 addresses to DNS servers. |
| WAN uptime | Time since last disconnect for IPv4 and IPV6 WAN connection. |
Voice
The Voice panel shows the status of the ringing schedule connected phone lines.
The Voice panel is not available in certain regions.
Profile
The Profile panel shows the network profiles configured on your device, if any.
The network profiles are configured by the manufacturer for each device type.
Depending on the network profile selected, additional panels may be displayed in the overview.
Voice
The Voice provides access to settings relating to voice communications through the device.
Voice Lines
The Voice Lines view shows a list of available voice lines for the device and allows you to configure them.
Advanced Settings
The Advanced Settings view contains advanced settings for SIP , voice lines and dial plans.
Number Blocking
The Number Blocking view allows you to block outgoing calls to specific numbers or or number ranges.
Ringing Schedule
The Ringing Schedule view lets you define when telephones should be allowed to ring.
Speed Dialing
The Speed Dialing view lets you configure a set of shortcode numbers that convert to the specified numbers when dialled.
Call Log
The Call Log view shows a list of the recent calls handled through the device.
| Item | Description |
|---|---|
| Date | Date for the call. |
| Time | Time for the call. |
| External Number | Calling number. |
| Internal Number | Receiving number. |
| Duration | Duration of the call. |
SIP Accounts
The SIP Accounts view shows information about configured SIP accounts for the device.
At the top of the page is a list of selectable accounts.
When a particular account is selected, details about it is shown in the configuration section.
| Item | Description |
|---|---|
| Enabled | Turn account on or off. |
| Account Name | Name of SIP account. |
| SIP domain name | Name of SIP domain. |
| SIP Username | The SIP account username for the account. |
| SIP Authentication Name | SIP Authentication Name used with password to register with SIP server. |
| SIP Password | Enter new password to change. |
| Show Key Text | Display the password. |
| Display Name | Display name used in Caller ID. |
| SIP Server/Registrar | Address for SIP server. |
| SIP Server/Registrar Port | Port for SIP server. |
| SIP Outbound Proxy | Address for outbound proxy. |
| SIP Outbound Proxy Port | Port for outbound proxy. |
| Incoming Phone Lines | Check boxes for connected phone line ports. |
| Preferred codecs | Order of preference for SIP codecs. |
| G.711MuLaw Packetization | Packetization setting for G.711MuLaw. |
| G.726 Packetization | Packetization setting for G.726. |
| G.729a Packetization | Packetization setting for G.711ALaw. |
| G.G.729a Packetization | Packetization setting for G.729a. |
| Autoframing | Negotiate packetization when call is established. |
| SIP Transport | UDP / TCP / TLS |
| Encryption | Use Secure Real-time Transport Protocol. |
| Use as Fax | Indicate that this SIP account will be used for a fax machine. This will force some settings. |
| Mailbox | Voicemail inbox. |
Add account
You can add as many accounts as you needed.
To add a account:
- Click the Add button
- Enter a Name for the account
- Enter values as needed.
- Click Apply
SIP Users
The SIP Users view shows information about configured SIP users for the device.
View
At the top of the page is a list of selectable accounts.
When a particular account is selected, details about it is shown in the configuration section.
| Item | Description |
|---|---|
| Enabled | Turn user on or off. |
| Name | Display name used in Caller ID. |
| Extension | Extension for this user. |
| User Name | SIP user name. |
| User Password | Enter new password to change. |
| Show Key Text | Display the password. |
| Call out using SIP provider | SIP account for outbound calls. |
| Mailbox | Voicemail inbox. |
| Preferred codecs | Order of preference for SIP codecs. |
| Host | Specific host for this user. |
| Qualify | Check that the user is reachable. |
Add user
You can add as many users as you needed.
To add a user:
- Click the Add button
- Enter a Name for the user
- Enter values as needed.
- Click Apply
Voice Lines
The Voice Lines view shows a list of available voice lines for the device and allows you to configure them.
Each available voice line has its own panel. Detailed information about each line is shown when you expand the panel.
The panels allow you to configure individual voice lines.
| Item | Description |
|---|---|
| Name | Identifier for the DECT line. |
| Internal Number | Diect call number. |
| Outgoing Calls Number | SIP account for external calls. |
| Call Waiting | Enable call waiting notification. |
| Call ID Restriction | Hide caller ID. |
| Voice Activity Detection | Detect voice (Transparent / Aggressive / Conservative). |
| Comfort Noise Generation | Generated noise (White / Hot / Spectrum estimate). |
| Echo cancellation | Remove echoes. |
| Transmit gain | Increase transmitted signal. |
| Receive gain | Increase received signal. |
Advanced Settings
The Advanced Settings view contains advanced settings for SIP , voice lines and dial plans.
Dial Plan
The Custom Dial plan view allows you to configure dialling digits for various services and networks.
SIP
The Advanced SIP Settings view lets you configure detailed parameters for your SIP services.
| Item | Description |
|---|---|
| Sip Proxy servers | Proxies to allow incoming calls from. |
| Bind Interface | Restrict listening to particular WAN interface. |
| Bindport | Port to use for UDP listening. |
| User Agent | Custom User-Agent information in the SIP header. |
| RTP Port Range | Ports to use for RTP |
| DTMF Mode | Mode for DTMF (Compatibility / RFC 2833 / SIP INFO / Inband). |
| Register Interval | Time in seconds between registration attempts. |
| Realm | SIP Realm for digest authentication. |
| Localnet | Network addresses that are considered inside of the NAT network. |
| Register Attempts | Number of registration attempts before giving up. |
| Register Timeout | Time before giving up a registration attempt. |
| Register Back-off Attempts | Number of attempts before back-off. |
| Register Back-off Timeout | Time in back-off before giving up attempt to register. |
| Remote Hold | Send hold events to proxy (Let network handle music on hold). |
| SRV Lookup | Enable DNS SRV lookup. |
| DNS Manager | Enable Asterisk DNS manager. |
| DNS Manager Refresh Interval | Refresh interval for the DNS manager. |
| Line suffix in contact header | Add suffix to SIP contact header with information about called lines. |
| SIP DiffServ | Differentiated services type of service for SIP data. |
| Audio DiffServ | Differentiated services type of service for audio data. |
| Congestion tone | Tone to play on congestion. (Congestion / Info) |
| STUN server | STUN service provider. |
| TLS/SSL Version | TLS v1 / TLS v2 / TLS v3. |
| Cipher string | Cipher identifier string. |
| Trusted CA | Public key for a trusted Certificate Authority. |
Trusted CA Certificate
To add a Trusted CA Certificate key:
- Click Add
- Copy the public key
- Paste the key into the window
- Click Save
- Click Apply
Line
The Advanced Line Settings view lets you configure detailed parameters for your voice lines .
| Item | Description |
|---|---|
| Locale selection | Country for device location. |
| Enable Jitter Buffer | Turn jitter prevention buffer on or off. |
| Force Jitter Buffer | Forces the receiver to use a jitter buffer. |
| Jitter Buffer implementation | The type of jitter buffer Fixed / Adaptive. |
| Maximum Jitter Buffer size | Size of jitter buffer (ms). |
| Enable Packet Loss Concealment | Turn PLC on or off. |
| Inter-digit timeout | Time between dialled digits before timing out (ms). |
Dial Plan
The Custom Dial plan view allows you to configure dialling digits for various services and networks.
| Item | Description |
|---|---|
| Enable incoming | Turn dial plan on or off for incoming calls. |
| Enable outgoing | Turn dial plan on or off for outgoing calls. |
| Enable custom hangup | Turn custom hang up on or off. |
| All Ports Extension | Port test extension. |
| Test Audio Extension | Audo tests the audio quality. |
| Test Echo Extension | Echo returns the outgoing audio from a channel back to the channel. |
Number Blocking
The Number Blocking view allows you to block outgoing calls to specific numbers or or number ranges.
Outgoing
| Item | Description |
|---|---|
| Outgoing Number Blocking | Turn blocking on or off for outgoing calls. |
| Do not allow connections to these numbers | List of blocked numbers. |
| Block connections to all foreign numbers | Block calls to different locales. |
| Block connections to all special rate numbers | Block calls to premium rate or pay services. |
Incoming
| Item | Description |
|---|---|
| Incoming Number Blocking | Turn blocking on or off for incoming calls. |
| Do not allow connections from these numbers | List of blocked numbers. |
Block number
To block a number:
- Click in the Phone extension box
- Enter the number
- Click outside of the Phone extension box
- Click Apply
Block number range
Ringing Schedule
The Ringing Schedule view lets you define when telephones should be allowed to ring.
| Item | Description |
|---|---|
| Ringing Schedule | Turn the schedule on or off. |
| During the times below ringing is | Enabled / Disabled. |
| Day | List of days when status applies. |
| Time | Time interval when status applies. |
| Status | Enabled / Disabled. |
Speed Dialing
The Speed Dialing view lets you configure a set of shortcode numbers that convert to the specified numbers when dialled.
The speed dialling list consists of the numbers 0 to 9. For each of these, you can add a number or extension that will be called when somebody dials the number.
| Item | Description |
|---|---|
| Speed Dialing | Turn speed dialling on or off. |
| Remove all entries from speed dial list | Clears the list |
DECT Radio
The Dect Radio view allows you to configure DECT radio settings.
Network
The Network view provides access to the devices, connections and available configurations in the network.
Connections
The Connections view allows you configure various connection interfaces to use in your device.
Routes
Static routes are useful if you have several networks accessible from your router and you want to correctly route packets between them.
Firewall
The firewall lets you filter traffic, set up port forwarding or expose particular services to the outside world.
Quality Of Service
The Quality Of Service view allows you to configure parameters for Quality of Service through applying groups of classes to interfaces.
MultiWAN
The MultiWAN view allows you to create and configure WAN traffic divisions for load balancing and failover and apply traffic rules.
Devices
The Devices view allows you to configure settings for various network types.
Base Device
The Base Device view shows you a list of devices that are used to access the network.
Device Status
The status of a device is indicated by the color of the icon.
| Color | Status |
|---|---|
| Green | Enabled and active |
| Black | Enabled, not active |
Note: These are the default colors. Your operator may use a different coloring scheme.
Ethernet
The Ethernet view allows you to configure the physical ethernet interfaces of your device.
The configuration is divided into multiple sections.
| Section | Description |
|---|---|
| Interface List | List of selectable the connected ethernet port devices. |
| Port Speed | Configuration of transmission speed, duplex setting and auto-negotiation. |
| Internet Port | Hardware port to use for Internet traffic. |
| Bridge | Setting to enable network bridge use. |
Port Speed
Port speed settings affect how a LAN or WAN port negotiates the speed setting.
Negotiation can be turned off (speed setting: only) or use Autonegotiation (speed setting max) to determine actual speed.
Communication on a port can be either half or full duplex.
A port that is set to disabled does not handle any traffic.
ADSL
The ADSL view allows you to configure ADSL devices.
At the top of the page is a list of selectable devices.
When a particular device is selected, details about it is shown in the configuration section.
| Section | Description |
|---|---|
| Name | Name of the device. |
| VPI | ATM Virtual Path Identifier. |
| VCI | ATM Virtual Channel Identifier. |
| DSL Link Type | EoA / PPPoE / IPoE. |
| Encapsulation Mode | LLC SNAP / VC-MUX. |
| Service Type | Service Type. |
| Bridge | Setting to enable network bridge use. |
Service Type
Service types define the guaranteed level of service in a ATM network. This involves such things as the timing between the source and destination, the guaranteed bandwidth and how many cells get lost in transmission.
| Setting | Description |
|---|---|
| UBR without PCR | Use Unspecified Bit Rate without Peak Cell Rate. |
| UBR with PCR | Use Unspecified Bit Rate with Peak Cell Rate. |
| CBR | Use Constant Bit Rate. |
| Non-Realtime VBR | Use Non-Real-Time Variable Bit Rate. |
| Realtime VBR | Use Real-Time Variable Bit Rate. |
VDSL
The VDSL view allows you to configure VDSL devices.
At the top of the page is a list of selectable devices.
When a particular device is selected, details about it is shown in the configuration section.
| Section | Description |
|---|---|
| Name | Name of the device. |
| DSL Latency Path | DSL Latency Path 1, 2 or both 1 & 2. |
| PTM Priority | Normal or High PTM Priority . |
| IP QoS Schedule Algorithm | Strict Priority Precedence / Weighted Fair Queuing. |
| Bridge | Setting to enable network bridge use. |
Latency Path
The DSL Latency Path comes in three modes: Path 1 (Fast), Path 2 (Interleaved) and Both 1 & 2. Fast is used for applications sensitive to delay. Interleaved suits applications sensitive to errors.
PTM Priority
The PTM Proprity defines how PTM traffic packets should be handled.
| Priority | Description |
|---|---|
| Normal Priority | Send packets according to their priority. |
| High Priority | Use preemption; lower-priority packets are paused when higher-priority packets are sent. |
IP Quality of Service Algorithm
The IP Quality of Service Algorithm determines which type of QoS to provide.
Strict Priority Precedence means that where the the packets with the highest priority always are sent first.
Weighted Fair Queuing means that bandwidth is adjusted automatically according to traffic priority and weight value.
VLAN
The VLAN view allows you to configure VLAN devices.
At the top of the page is a list of selectable devices.
When a particular device is selected, details about it is shown in the configuration section.
| Section | Description |
|---|---|
| Name | Name of the device. |
| Base Device | Base Device to create interface for. |
| 802.1q | 802_1q tag. |
| 802.1p | 802_1q priority. |
| Bridge | Setting to enable network bridge use. |
802.1q
IEEE 802.1Q is a standard for Ethernet VLANs where VLANs are given a numeric tag. The tag is used to identify traffic in networks, and decide how to handle it.
This allows multiple bridged networks to share the same physical link without leaking information to each other networks.
802.1p
802.1p is a standard for priority levels, identifying the class of service a VLAN is to be used for. There are 8 different levels, numbered from 0 to 7.
| Priority | Acronym | Traffic types | Comment |
|---|---|---|---|
| 0 | BK | Background | Lowest |
| 1 | BE | Best Effort | |
| 2 | EE | Excellent Effort | |
| 3 | CA | Critical Applications | |
| 4 | VI | Video | < 100 ms latency and jitter |
| 5 | VO | Voice | < 10 ms latency and jitter |
| 6 | IC | Internetwork Control | |
| 7 | NC | Network Control | Highest |
XDSL
The xDSL view allows you to configure line settings and profiles.
The xDSL settings are divided into several tabs.
Modulation
The modulation tab lets you turn various line modulations on or off.
| Profile | Description | Down Mbit/s | Up Mbit/s |
|---|---|---|---|
| G.Dmt | G.Dmt modulation. | 12 | 1.3 |
| G.lite | G.lite modulation. | 1.5 | 0.5 |
| T.1413 | T.1413 modulation. | 8.1 | 1.5 |
| ADSL2 | ADSL2 modulation. | 12 | 1.0 |
| AnnexL | AnnexL modulation. | 5 | 0.8 |
| ADSL2+ | ADSL2+ modulation. | 24 | 1.0 |
| AnnexM | AnnexM modulation. | 24 | 3.5 |
| VDSL2 | VDSL2 modulation. | 100 | 100 |
VDSL Profile
The VDSL Profile tab lets you turn various VDSL2 profiles on or off.
| Profile | Bandwidth (MHz) | Downstream carriers | Carrier bandwidth (kHz) | Maximum downstream transmit power (dBm) | Max. downstream throughput (Mbit/s) |
|---|---|---|---|---|---|
| 8a | 8.832 | 2048 | 4.3125 | +17.5 | 50 |
| 8b | 8.832 | 2048 | 4.3125 | +20.5 | 50 |
| 8c | 8.5 | 1972 | 4.3125 | +11.5 | 50 |
| 8d | 8.832 | 2048 | 4.3125 | +14.5 | 50 |
| 12a | 12 | 2783 | 4.3125 | +14.5 | 68 |
| 12b | 12 | 2783 | 4.3125 | +14.5 | 68 |
| 17a | 17.664 | 4096 | 4.3125 | +14.5 | 100 |
Capabilities
The capabilites tab lets you turn various xDSL capabilites on or off.
| Profile | Description | Comment |
|---|---|---|
| US0 | Upstream 0 Band. | 20 to 138 kHz |
| Bitswap | Bitswap. | Used for DMT modulation. |
| SRA | Seamless Rate Adaptation. |
Connections
The Connections view allows you configure various connection interfaces to use in your device.
View
This page allows to configure IP addresses used in your home network. In case DHCP is used, your router automatically assignes an IP address to devices connected to the network.
The page contains a list of interfaces, with one widget for each interface.
Connection Buttons
Connect
To turn a connection on:
- Select the connection you are interested in
- Click Connect button
Disconnect
To turn a connection off:
- Select the connection you are interested in
- Click Disconnect button
Edit
To change the settings for a connection:
- Select the connection you are interested in
- Click Edit button
The connection editor is shown below the connection list.
Connection Editor
You can view, manage and configure the settings for interfaces from the connections page.
Main Buttons
Delete
To change the settings for a connection:
- Select the connection you are interested in
- Click Edit button
Add
To add new connection interface:
- Select the connection you are interested in
- Click Edit button
The new interface dialog is shown.
Create Connection Wizard
The Create New Network Interface wizard allows you to create a new interface according to your needs through a number of dialogs.
Create Connection Wizard
The Create New Network Interface wizard allows you to create a new interface according to your needs through a number of dialogs.
Create Connection
The dialog is a wizard where you add information in several steps.
The number of steps and their contents varies depending on the type of interface you create.
Note: As a last step you finalize the setup, but you can further edit the settings from the connections page.
Connection Types
In the first step, you can choose the type of interface: Uplink, Downlink, or Unmanaged.
Depending on your choice in the first step, different options become available.
Uplink
An uplink interface type is an interface to services.
Interfaces
Point-to-Point Protocol over Ethernet
A Point-to-Point Protocol over Ethernet connection uses PPPoE to establish the network.
Point-to-Point Protocol over ATM
A Point-to-Point Protocol over ATM connection uses PPPoA to establish the network.
Point-to-point Tunnel
WWAN (LTE/HSPA+)
WWAN
A Wireless Wide Area Network (WWAN), is a wireless network that extends over a large geographical distance.
HSPA / HSPA+
High Speed Packet Access (HSPA) is an extension of 3G mobile networks utilizing WCDMA.
Evolved High Speed Packet Access (HSPA+) is a furhter improvement on HSPA allowing for higher speeds.
Wizard
Step 1
In the first step you select basic settings for the interface.
| Item | Description |
|---|---|
| Interface Name | Name for the interface. |
| Interface Type | Select interface protocol type. |
Finalize
In the final step you select protocol and firewall settings for the interface.
| Item | Description |
|---|---|
| Protocol | Select protocol. |
| Add network to a firewall zone | Connects interface to firewall zone. |
DHCP v4
An DHCP v4 connection uses an IPv4 address provided by a DHCP server.
IPv4
Internet Protocol Version 4 - IPv4 - is the first major version of the Internet Protocol.
Wizard
Step 1
In the first step you select basic settings for the interface.
| Item | Description |
|---|---|
| Interface Name | Name for the interface. |
| Interface Type | Select interface protocol type. |
Finalize
In the final step you select protocol, adapter and firewall settings for the interface.
| Item | Description |
|---|---|
| Protocol | Select protocol. |
| Interface Type | Select interface protocol type. |
| Ethernet Adapter | Base Device to create interface for. |
| Add network to a firewall zone | Connects interface to firewall zone. |
DHCP v6 (Uplink)
An DHCP v6 connection uses an IPv6 address provided by a DHCP server.
Wizard
Step 1
In the first step you select basic settings for the interface.
| Item | Description |
|---|---|
| Interface Name | Name for the interface. |
| Interface Type | Select interface protocol type. |
Finalize
In the final step you select protocol, adapter and firewall settings for the interface.
| Item | Description |
|---|---|
| Protocol | Select protocol. |
| Interface Type | Select interface protocol type. |
| Ethernet Adapter | Base Device to create interface for. |
| Add network to a firewall zone | Connects interface to firewall zone. |
Point-to-Point Protocol
A Point-to-Point Protocol connection uses PPP to establish the network.
PPP
Point-to-Point Protocol (PPP) is a protocol for providing a direct data link connection with authentication, encryption and compression.
Wizard
Step 1
In the first step you select basic settings for the interface.
| Item | Description |
|---|---|
| Interface Name | Name for the interface. |
| Interface Type | Select interface protocol type. |
Finalize
In the final step you select protocol and firewall settings for the interface.
| Item | Description |
|---|---|
| Protocol | Select protocol. |
| Add network to a firewall zone | Connects interface to firewall zone. |
Point-to-Point Protocol over Ethernet
A Point-to-Point Protocol over Ethernet connection uses PPPoE to establish the network.
Wizard
Step 1
In the first step you select basic settings for the interface.
| Item | Description |
|---|---|
| Interface Name | Name for the interface. |
| Interface Type | Select interface protocol type. |
Finalize
In the final step you select protocol and firewall settings for the interface.
| Item | Description |
|---|---|
| Protocol | Select protocol. |
| Ethernet Adapter | Base Device to create interface for. |
| Add network to a firewall zone | Connects interface to firewall zone. |
Point-to-Point Protocol over ATM
A Point-to-Point Protocol over ATM connection uses PPPoA to establish the network.
Wizard
Step 1
In the first step you select basic settings for the interface.
| Item | Description |
|---|---|
| Interface Name | Name for the interface. |
| Interface Type | Select interface protocol type. |
Finalize
In the final step you select protocol and firewall settings for the interface.
| Item | Description |
|---|---|
| Protocol | Select protocol. |
| Ethernet Adapter | Base Device to create interface for. |
| Add network to a firewall zone | Connects interface to firewall zone. |
3G
3G
Third-generation wireless telephone technology (3G), is a cellular network for digital mobile data communication for broadband traffic.
Wizard
Step 1
In the first step you select basic settings for the interface.
| Item | Description |
|---|---|
| Interface Name | Name for the interface. |
| Interface Type | Select interface protocol type. |
Finalize
In the final step you select protocol and firewall settings for the interface.
| Item | Description |
|---|---|
| Protocol | Select protocol. |
| Add network to a firewall zone | Connects interface to firewall zone. |
Point-to-point Tunnel
Point-to-Point Tunneling Protocol
Point-to-Point Tunneling Protocol (PTPT) is a technology for virtual private networks through TCP and a GRE with PPP packets.
Wizard
Step 1
In the first step you select basic settings for the interface.
| Item | Description |
|---|---|
| Interface Name | Name for the interface. |
| Interface Type | Select interface protocol type. |
Finalize
In the final step you select protocol and firewall settings for the interface.
| Item | Description |
|---|---|
| Protocol | Select protocol. |
| Add network to a firewall zone | Connects interface to firewall zone. |
IPv6 Tunnel in IPv4
A IPv6 Tunnel in IPv4 connection uses IPv4 to transmit IPv6 traffic.
Wizard
Step 1
In the first step you select basic settings for the interface.
| Item | Description |
|---|---|
| Interface Name | Name for the interface. |
| Interface Type | Select interface protocol type. |
Finalize
In the final step you select protocol and firewall settings for the interface.
| Item | Description |
|---|---|
| Protocol | Select protocol. |
| Add network to a firewall zone | Connects interface to firewall zone. |
IPv6 Tunnel to IPv4
A IPv6 Tunnel to IPv4 connection uses IPv4 to transmit IPv6 traffic.
Wizard
Step 1
In the first step you select basic settings for the interface.
| Item | Description |
|---|---|
| Interface Name | Name for the interface. |
| Interface Type | Select interface protocol type. |
Finalize
In the final step you select protocol and firewall settings for the interface.
| Item | Description |
|---|---|
| Protocol | Select protocol. |
| Add network to a firewall zone | Connects interface to firewall zone. |
IPv6 rapid deployment
A IPv6 rapid deployment interface for IPv4 infrastructures.
Wizard
Step 1
In the first step you select basic settings for the interface.
| Item | Description |
|---|---|
| Interface Name | Name for the interface. |
| Interface Type | Select interface protocol type. |
Finalize
In the final step you select protocol and firewall settings for the interface.
| Item | Description |
|---|---|
| Protocol | Select protocol. |
| Add network to a firewall zone | Connects interface to firewall zone. |
Downlink
A Downlink interface is an interface to subscribers/clients.
Finalize
In the final step you select protocol and firewall settings for the interface.
| Item | Description | Applies to |
|---|---|---|
| Interface Type | Select interface type (Standalone / Anywan / Bridge). | |
| Physical Device | Device(s) to use for the connection. | |
| Add network to a firewall zone | Connects interface to firewall zone. |
Physical Device
For Standalone, you need to select the base device to use for the connection.
For Anywan and Bridge, you need to add a physical device to use for the connection.
| Item | Description | Applies to |
|---|---|---|
| Ethernet Adapter | Selector for base device to use for the connection. | Standalone |
| Add Device | Dialog to select network device to use for the connection. | Anywan / Bridge |
Ethernet Adapter
- Select a base device from the dropdown menu.
Add Device
- Click Add
The Select Network Device dialog is shown.
- Select a network device from the dropdown menu
Unmanaged
The interface protocol type Unmanaged means that the connection has no defined protocol.
Step 1
In the first step you select basic settings for the interface.
| Item | Description |
|---|---|
| Interface Type | Select interface type. |
| Add/Remove Devices | Select interface protocol type. |
- Select Interface Type
- Add as many devices as needed
Add Device
- Click Add
The Add Device dialog is shown.
- Select a network device from the dropdown menu
- Click OK
Finalize
- Click OK again
- Click Apply
Connection Editor
You can view, manage and configure the settings for interfaces from the connections page.
Edit Connections
To edit a connection:
- Click Edit button
The Connection Section is displayed at the bottom of the page.
The connection section consists of a number of tabs, showing details the connection.
Depending on connection type the tabs will be different, but the standard tabs are General, Physical Settings, and Advanced.
Additional tabs become visible as they are needed.
Default Connections
Connection Types
Point-to-Point Protocol over Ethernet
A Point-to-Point Protocol over Ethernet connection uses PPPoE to establish the network.
Point-to-Point Protocol over ATM
A Point-to-Point Protocol over ATM connection uses PPPoA to establish the network.
Point-to-point Tunnel
IPv6 rapid deployment
A IPv6 rapid deployment interface for IPv4 infrastructures.
Edit (ade:network:connections:6rd:start)
Dual-Stack Lite
A Dual-Stack Lite connection uses DS-Lite through an Address Family Transition Router to establish the network.
Point-to-Point Protocol over L2TP
A Point-to-Point Protocol over L2TP connection uses PPP and L2TP server to establish the network.
LAN
The default LAN connection is a DHCP v4 connection using a static IPv4 address.
IPv4
Internet Protocol Version 4 - IPv4 - is the first major version of the Internet Protocol.
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
DHCP
The DHCP tab allows you to enable and use a specific DHCP server for the connection.
View
| Item | Description |
|---|---|
| DHCP Server | Turn DHCP Server on or off. |
| DHCP Pool Start | Start IP number for the DHCP Pool start number IP address |
| DHCP Pool Size | Number of IP addresses in the DHCP Pool |
| DHCP Lease Time | DHCP Lease Time for the LAN. |
| Static DHCP | Reserve an IP address DHCP Lease for a connected device. |
Additional Sections
Advanced
The Advanced section contains advanced DHCP options.
View
| Item | Description | Comment |
|---|---|---|
| DHCP Options | DHCP Option ID and value to assign. | |
| Dynamic DHCP | Use Dynamic DHCP. | If disabled, only clients with static leases will be allowed. |
| Force | Override existing options. |
IPv6 Settings
The DHCP tab allows you to enable and use a specific DHCP server for the connection.
View
| Item | Description | Comment |
|---|---|---|
| DHCPv6 Service | Service handling DHCP services for IPv6. | server / relay / disabled |
| Router Advertisement Service | Service handling Router Advertisement. | server / relay / disabled |
| NDP-Proxy | NDP proxy. | relay / none |
Values
| Value | Description |
|---|---|
server | Provide service. |
relay | Forward messages. |
disabled | Turn service off. |
none | Do not provide this service. |
Static DHCP
The Static DHCP tab lets you add fixed IP address for connected clients.
View
| Device Name | Turn DHCP Server on or off. |
| MAC Address | MAC address. |
| IP Address | IP address. |
| DUID (IPv6) | IPv6 DUID. |
| Host ID (IPv6) | IPv6 Host ID. |
| Tag | Tag with further DHCP Options as configured in the DHCP/DNS settings. |
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
Protocol
The protocol section contains detailed settings for the connection.
IPv4
The IPv4 section contains IP configuration.
| Item | Description |
|---|---|
| IPv4 Address | Device DHCP address |
| IPv4 Subnet Mask | IPv4 Subnet Mask |
| IPv4 Broadcast Mask | IPv4 Broadcast Mask |
IPv6
The IPv6 section contains IP configuration.
| Item | Description | Comment |
|---|---|---|
| IPv6 Assignment Length | Number betwen 48 and 64. |
|
| IPv6 Assigned Prefix Hint | Hexadecimal number between 1 and FFFF |
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
| Section | Description |
|---|---|
| Interface type | The connection interface type. |
| Ethernet Adapter | Selector for base device to use for the connection. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
Add/Remove custom DNS Servers
These DNS entries will be applied on the interface
You can add as many custom DNS servers as you like, but they must be unique.
Note: These custom DNS entries only affect the interface where they are added.
To add a custom DNS server:
- Add the IP numbers to the DNS server
- Click Save
To remove a custom DNS server:
- Click Save
WAN
The default WAN connection uses an IPv4 address provided by a DHCP server.
IPv4
Internet Protocol Version 4 - IPv4 - is the first major version of the Internet Protocol.
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
| Hostname | Hostname to use for DHCP requests. |
| Create default route | Automatically generated routing information. |
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
| Section | Description |
|---|---|
| Interface type | The connection interface type. |
| Add/Remove Devices | Devices to associate with the connection. |
| Ethernet Adapter | Selector for base device to use for the connection. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
| Use broadcast flag | Add broadcast flag to traffic. |
| Use default gateway | Use default route. |
| Use DNS servers advertised by peer | Use DHCP DNS server. |
Add/Remove custom DNS Servers
You can add as many custom DNS servers as you like, but they must be unique.
To add a custom DNS server:
- Add the IP numbers to the DNS server
- Click Save
To remove a custom DNS server:
- Click Save
DHCP Options
| Item | Description |
|---|---|
| Additional DHCP options to request from the server | DHCP option ID:s for additional options. |
| Client ID to send when requesting DHCP | Custom ID to use for DHCP requests. |
| Vendor Class to send when requesting DHCP | Use for device-specific DHCP options. |
WAN6
The default WAN6 connection is a IPv6 address provided by a DHCP server.
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
| Request IPv6 Address | Try / Force / None |
| Request Prefix Length | 48 / 52 / 56 / 60 / 64 / Auto / Disabled |
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
| Section | Description |
|---|---|
| Interface type | The connection interface type. |
| Add/Remove Devices | Devices to associate with the connection. |
| Ethernet Adapter | Selector for base device to use for the connection. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
| Use default gateway | Use default route. |
| Use DNS servers advertised by peer | Use DHCP DNS server. |
Add/Remove custom DNS Servers
You can add as many custom DNS servers as you like, but they must be unique.
To add a custom DNS server:
- Add the IP numbers to the DNS server
- Click Save
To remove a custom DNS server:
- Click Save
DHCP Options
| Item | Description |
|---|---|
| Custom delegated IPv6-prefix | Prefix for prefix delegation. |
| Client ID to send when requesting DHCP | Custom ID to use for DHCP requests. |
Unmanaged
An unmanaged connection has no predefined protocol for the connection.
Unmanaged
The interface protocol type Unmanaged means that the connection has no defined protocol.
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
Bridge Devices
The bridge devices section lets you add or remove bridged devices to the connection.
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
Static Address
A static address uses a fixed IP address for the connection.
Static address
A static IP address is an address that doesn't change, unless manually changed by the administrator.
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
Protocol
The protocol section contains detailed settings for the connection.
IPv4
The IPv4 section contains IP configuration.
| Item | Description |
|---|---|
| IPv4 Address | Device DHCP address |
| IPv4 Subnet Mask | IPv4 Subnet Mask |
| IPv4 Broadcast Mask | IPv4 Broadcast Mask |
Add/Remove custom DNS Servers
You can add as many custom DNS servers as you like, but they must be unique.
To add a custom DNS server:
- Add the IP numbers to the DNS server
- Click Save
To remove a custom DNS server:
- Click Save
IPv6
The IPv6 section contains IP configuration.
| Item | Description | Comment |
|---|---|---|
| IPv6 Assignment Length | Number betwen 48 and 64. |
|
| IPv6 Assigned Prefix Hint | Hexadecimal number between 1 and FFFF |
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
| Section | Description |
|---|---|
| Interface type | The connection interface type. |
| Ethernet Adapter | Selector for base device to use for the connection. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
DHCP
The DHCP tab allows you to enable and use a specific DHCP server for the connection.
Basic
| Item | Description |
|---|---|
| DHCP Server | Turn DHCP Server on or off. |
| DHCP Pool Start | Start IP number for the DHCP Pool start number IP address |
| DHCP Pool Size | Number of IP addresses in the DHCP Pool |
| DHCP Lease Time | DHCP Lease Time for the LAN. |
| Static DHCP | Reserve an IP address DHCP Lease for a connected device. |
Advanced
IPv6
DHCP v4
An DHCP v4 connection uses an IPv4 address provided by a DHCP server.
IPv4
Internet Protocol Version 4 - IPv4 - is the first major version of the Internet Protocol.
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
| Hostname | Hostname to use for DHCP requests. |
| Create default route | Automatically generated routing information. |
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
| Section | Description |
|---|---|
| Interface type | The connection interface type. |
| Add/Remove Devices | Devices to associate with the connection. |
| Ethernet Adapter | Selector for base device to use for the connection. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
| Use broadcast flag | Add broadcast flag to traffic. |
| Use default gateway | Use default route. |
| Use DNS servers advertised by peer | Use DHCP DNS server. |
Add/Remove custom DNS Servers
You can add as many custom DNS servers as you like, but they must be unique.
To add a custom DNS server:
- Add the IP numbers to the DNS server
- Click Save
To remove a custom DNS server:
- Click Save
DHCP Options
| Item | Description |
|---|---|
| Additional DHCP options to request from the server | DHCP option ID:s for additional options. |
| Client ID to send when requesting DHCP | Custom ID to use for DHCP requests. |
| Vendor Class to send when requesting DHCP | Use for device-specific DHCP options. |
DHCP v6
An DHCP v6 connection uses an IPv6 address provided by a DHCP server.
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
| Request IPv6 Address | Try / Force / None |
| Request Prefix Length | 48 / 52 / 56 / 60 / 64 / Auto / Disabled |
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
| Section | Description |
|---|---|
| Interface type | The connection interface type. |
| Add/Remove Devices | Devices to associate with the connection. |
| Ethernet Adapter | Selector for base device to use for the connection. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
| Use default gateway | Use default route. |
| Use DNS servers advertised by peer | Use DHCP DNS server. |
Add/Remove custom DNS Servers
You can add as many custom DNS servers as you like, but they must be unique.
To add a custom DNS server:
- Add the IP numbers to the DNS server
- Click Save
To remove a custom DNS server:
- Click Save
DHCP Options
| Item | Description |
|---|---|
| Custom delegated IPv6-prefix | Prefix for prefix delegation. |
| Client ID to send when requesting DHCP | Custom ID to use for DHCP requests. |
Point-to-Point Protocol
A Point-to-Point Protocol connection uses PPP to establish the network.
PPP
Point-to-Point Protocol (PPP) is a protocol for providing a direct data link connection with authentication, encryption and compression.
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
| Hostname | Hostname to use for DHCP requests. |
| Create default route | Automatically generated routing information. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
| Enable IPv6 on the PPP link | Enables IPv6 connection from the provider. |
| Use default gateway | Use default route. |
| Use DNS servers advertised by peer | Use DHCP DNS server. |
Add/Remove custom DNS Servers
You can add as many custom DNS servers as you like, but they must be unique.
To add a custom DNS server:
- Add the IP numbers to the DNS server
- Click Save
To remove a custom DNS server:
- Click Save
LCP Options
The LCP options section contains LCP configuration.
| Item | Description | Comment |
|---|---|---|
| LCP echo failure threshold | Number of echo failures before peer is considered dead. | Use 0 to ignore failures. |
| LCP echo interval | How often to send echo-requests. | Used together with failure threshold. |
| Inactivity timeout | Time until inactive connection is closed. | Use 0 to persist connection. |
Point-to-Point Protocol over Ethernet
A Point-to-Point Protocol over Ethernet connection uses PPPoE to establish the network.
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
| Section | Description |
|---|---|
| Ethernet Adapter | Selector for base device to use for the connection. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
| Enable IPv6 on the PPP link | Enables IPv6 connection from the provider. |
| Use default gateway | Use default route. |
| Use DNS servers advertised by peer | Use DHCP DNS server. |
Add/Remove custom DNS Servers
You can add as many custom DNS servers as you like, but they must be unique.
To add a custom DNS server:
- Add the IP numbers to the DNS server
- Click Save
To remove a custom DNS server:
- Click Save
LCP Options
The LCP options section contains LCP configuration.
| Item | Description | Comment |
|---|---|---|
| LCP echo failure threshold | Number of echo failures before peer is considered dead. | Use 0 to ignore failures. |
| LCP echo interval | How often to send echo-requests. | Used together with failure threshold. |
| Inactivity timeout | Time until inactive connection is closed. | Use 0 to persist connection. |
Point-to-Point Protocol over ATM
A Point-to-Point Protocol over ATM connection uses PPPoA to establish the network.
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
| Hostname | Hostname to use for DHCP requests. |
| Create default route | Automatically generated routing information. |
Physical Settings
The physical settings tab contains settings for hardware management and devices for the connection.
| Section | Description |
|---|---|
| Ethernet Adapter | Selector for base device to use for the connection. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
| Enable IPv6 on the PPP link | Enables IPv6 connection from the provider. |
| Use default gateway | Use default route. |
| Use DNS servers advertised by peer | Use DHCP DNS server. |
Add/Remove custom DNS Servers
You can add as many custom DNS servers as you like, but they must be unique.
To add a custom DNS server:
- Add the IP numbers to the DNS server
- Click Save
To remove a custom DNS server:
- Click Save
LCP Options
The LCP options section contains LCP configuration.
| Item | Description | Comment |
|---|---|---|
| LCP echo failure threshold | Number of echo failures before peer is considered dead. | Use 0 to ignore failures. |
| LCP echo interval | How often to send echo-requests. | Used together with failure threshold. |
| Inactivity timeout | Time until inactive connection is closed. | Use 0 to persist connection. |
3G
3G
Third-generation wireless telephone technology (3G), is a cellular network for digital mobile data communication for broadband traffic.
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
| Modem device | Modem to use for 3G traffic. |
| Service Type | Both UMTS and GPRS / Only UMTS / Only GPRS. |
| APN | Access Point Name. |
| PIN-Code | PIN code for identification. |
| PAP/CHAP Username | For authentication with PAP or CHAP. |
| PAP/CHAP Password | For authentication with PAP or CHAP. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
| Enable IPv6 on the PPP link | Enables IPv6 connection from the provider. |
| Use default gateway | Use default route. |
| Modem Init timeout | Use DHCP DNS server. |
| Use DNS servers advertised by peer | Use DHCP DNS server. |
Add/Remove custom DNS Servers
You can add as many custom DNS servers as you like, but they must be unique.
To add a custom DNS server:
- Add the IP numbers to the DNS server
- Click Save
To remove a custom DNS server:
- Click Save
LCP Options
The LCP options section contains LCP configuration.
| Item | Description | Comment |
|---|---|---|
| LCP echo failure threshold | Number of echo failures before peer is considered dead. | Use 0 to ignore failures. |
| LCP echo interval | How often to send echo-requests. | Used together with failure threshold. |
| Inactivity timeout | Time until inactive connection is closed. | Use 0 to persist connection. |
WWAN (LTE/HSPA+)
WWAN
A Wireless Wide Area Network (WWAN), is a wireless network that extends over a large geographical distance.
HSPA / HSPA+
High Speed Packet Access (HSPA) is an extension of 3G mobile networks utilizing WCDMA.
Evolved High Speed Packet Access (HSPA+) is a furhter improvement on HSPA allowing for higher speeds.
General
The general tab contains status information and settings relating to the protocol.
Status
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device in use. |
| Protocol | Protocol in use. |
Configuration
| Item | Description |
|---|---|
| Protocol | Protocol in use. |
| Modem device | Modem to use for 3G traffic. |
| APN | Access Point Name. |
| PIN-Code | PIN code for identification. |
| Authentication type | PAP / CHAP / Both / None . |
| Username | For authentication with PAP or CHAP. |
| Password | For authentication with PAP or CHAP. |
| Modes | Comma-separated list of allowed network modes (all / lte / umts / gsm / cdma / td-scdma). |
| Delay | Seconds to wait before trying to interact with the modem. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
4G
4G
Fourth-generation wireless telephone technology (4G), is a cellular network for digital mobile data communication for high-speed broadband.
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
| Modem device | Modem to use for 3G traffic. |
| APN | Access Point Name. |
| PIN-Code | PIN code for identification. |
| PAP/CHAP Username | For authentication with PAP or CHAP. |
| PAP/CHAP Password | For authentication with PAP or CHAP. |
| Hostname to send when requesting DHCP | Hostname to include in DHCP requests. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
| Use broadcast flag | Add broadcast flag to traffic. |
| Use default gateway | Use default route. |
| Use DNS servers advertised by peer | Use DHCP DNS server. |
Add/Remove custom DNS Servers
You can add as many custom DNS servers as you like, but they must be unique.
To add a custom DNS server:
- Add the IP numbers to the DNS server
- Click Save
To remove a custom DNS server:
- Click Save
DHCP Options
| Item | Description | Comment |
|---|---|---|
| Client ID to send when requesting DHCP | Custom ID to use for DHCP requests. | |
| Vendor Class to send when requesting DHCP | Use for device-specific DHCP options. |
Point-to-point Tunnel
Point-to-Point Tunneling Protocol
Point-to-Point Tunneling Protocol (PTPT) is a technology for virtual private networks through TCP and a GRE with PPP packets.
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
| VPN Server | Virtual Private Network server. |
| PAP/CHAP Username | For authentication with PAP or CHAP. |
| PAP/CHAP Password | For authentication with PAP or CHAP. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
| Enable IPv6 on the PPP link | Enables IPv6 connection from the provider. |
| Use default gateway | Use default route. |
| Use DNS servers advertised by peer | Use DHCP DNS server. |
Add/Remove custom DNS Servers
You can add as many custom DNS servers as you like, but they must be unique.
To add a custom DNS server:
- Add the IP numbers to the DNS server
- Click Save
To remove a custom DNS server:
- Click Save
LCP Options
The LCP options section contains LCP configuration.
| Item | Description | Comment |
|---|---|---|
| LCP echo failure threshold | Number of echo failures before peer is considered dead. | Use 0 to ignore failures. |
| LCP echo interval | How often to send echo-requests. | Used together with failure threshold. |
| Inactivity timeout | Time until inactive connection is closed. | Use 0 to persist connection. |
IPv6 Tunnel in IPv4
A IPv6 Tunnel in IPv4 connection uses IPv4 to transmit IPv6 traffic.
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
| Local IPv4 address | IPv4 address to use instead of WAN address. |
| Remote IPv4 address | Address to use tunnel broker Point of Presence |
| Local IPv6 address | Endpoint provided by the tunnel broker. |
| IPv6 routed prefix | Prefix to be used by clients. |
| Dynamic tunnel | Dynamic update of endpoint. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
| Use default gateway | Use default route. |
| Use TTL on tunnnel interface | Data Time To Live. |
IPv6 Tunnel to IPv4
A IPv6 Tunnel to IPv4 connection uses IPv4 to transmit IPv6 traffic.
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
| Local IPv4 address | IPv4 address to use instead of WAN address. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
| Use default gateway | Use default route. |
| Use TTL on tunnnel interface | Data Time To Live. |
IPv6 rapid deployment
A IPv6 rapid deployment interface for IPv4 infrastructures.
Edit (ade:network:connections:6rd:start)
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
| Local IPv4 address | IPv4 address to use instead of WAN address. |
| Remote IPv4 address | Address to the relay. |
| IPv6 prefix | Prefix assigned to provider. |
| IPv6 prefix length | no or 48 to 64 |
| IPv4 prefix length | Up to 43 bits. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
| Use default gateway | Use default route. |
| Use TTL on tunnnel interface | Data Time To Live. |
Dual-Stack Lite
A Dual-Stack Lite connection uses DS-Lite through an Address Family Transition Router to establish the network.
DS-Lite
Dual-Stack Lite (DS-Lite) is a method for sharing of IPv4 addresses by combining IPv4-in-IPv6 and NAT.
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
| DS-Lite AFTR address | Address to Address Family Transition Router. |
| Local IPv6 address | IPv6 address to use instead of WAN address. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
| Tunnel Link | Connection to use as tunnel link. |
| Use TTL on tunnnel interface | Data Time To Live. |
Point-to-Point Protocol over L2TP
A Point-to-Point Protocol over L2TP connection uses PPP and L2TP server to establish the network.
PPP
Point-to-Point Protocol (PPP) is a protocol for providing a direct data link connection with authentication, encryption and compression.
L2TP
Layer 2 Tunneling Protocol (L2TP) is a protocol used to support VPNs, where security is provided in the transmitted packages rather than in the tunneling.
General
The general tab contains status information and settings relating to the protocol.
| Item | Description |
|---|---|
| Status | Connection status. |
| Device | Device for the connection. |
| Protocol | Protocol in use. |
| L2TP Server | Address to Layer 2 Tunneling Protoco server. |
| PAP/CHAP Username | For authentication with PAP or CHAP. |
| PAP/CHAP Password | For authentication with PAP or CHAP. |
Advanced
The advanced tab contains settings for management of advanced features for the connection.
| Item | Description |
|---|---|
| Bring up on boot | Start the connection when device starts. |
| Use gateway metric | Gateway metric to use. |
| Override MAC address | Enforced MAC address to use. |
| Override MTU | MTU size to use. |
| Enable IPv6 on the PPP link | Enables IPv6 connection from the provider. |
| Use default gateway | Use default route. |
| Use DNS servers advertised by peer | Use DHCP DNS server. |
Add/Remove custom DNS Servers
Routes
Static routes are useful if you have several networks accessible from your router and you want to correctly route packets between them.
Add Static Route
To add a static route:
- Click the add button
- Enter information for the route fields.
- Click Apply
IPv4 Routes
The IPv4 section lets you add static routes for IPv4.
| Item | Description | |
|---|---|---|
| Interface | Affected connection for the route. | |
| Target | Destination IP address. | |
| Netmask | Applicable netmask. | |
| Gateway | IP address to the internet gateway. | |
| Metric | Route metric. | |
| MTU | MTU size to use. | |
| Delete | Remove route. |
IPv6 Routes
The IPv4 section lets you add static routes for IPv4.
| Item | Description | |
|---|---|---|
| Interface | Affected connection for the route. | |
| Target | Destination IP address. | |
| Gateway | IP address to the internet gateway. | |
| Metric | Route metric. | |
| MTU | MTU size to use. | |
| Delete | Remove route. |
Firewall
The firewall lets you filter traffic, set up port forwarding or expose particular services to the outside world.
Forwarding
Port Forwarding allows remote computers to connect to a specific device within your private network.
DMZ / Exposed Host
A local network device can be made an Exposed Host. It is placed in the DMZ outside of the firewall, which provides unrestricted Internet access to the network device.
General Settings
The general settings view allows you to turn the firewall on or off.
Firewall Settings
To enable the firewall:
- Click Enable Firewall
Zones
The Zones view lets you can configure firewall zones to group your firewall rules.
At the top of the page is a list of selectable zones.
By default this list contains the LAN and WAN zones, which contain default settings for local and Internet traffic.
When a particular interface is selected, details about it is shown in the configuration section.
Zone configuration
| Item | Description |
|---|---|
| Name | Identifier for the zone. |
| Default policy | Default behavior for various traffic. |
| Masquerading | Enable firewall masquerading. |
| MSS Clamping | MSS Clamping limit. |
| Allow forward to destination zones | Check zones to permit forwarding. |
| Allow forward from source zones | Check zones to permit forwarding. |
| Zone members | Interfaces that are part of the zone. |
Default Policy
The default policy setting defines firewall rules that apply unless specific rules override them.
| Item | Description |
|---|---|
| Input | Incoming traffic from WAN. |
| Output | Outgoing traffic to WAN. |
| Forward | Traffic from LAN to WAN. |
The different default policy values determine the firewall behavior, through the firewall actions:
Firewall Action
The firewall action defines how traffic is handled by the firewall.
| Item | Description |
|---|---|
| ACCEPT | Allow the traffic. |
| REJECT | Refuse the traffic. |
| DROP | Ignore the traffic. |
| FORWARD | Pass the traffic along. |
Add Firewall Zone
To add a firewall zone:
- Click the Add button
- Enter information in the fields
- Click Apply
Once the zone has been created, you can use it with your connections.
Add Zone Members
If you have networks/devices set up, you can add them to the zone.
To add a device as a zone member:
- Click the Add button
The Select network device dialog opens.
- Open the select network menu
- Select the device
- Click OK
- Click Apply
Rules
Firewall rules are more fine grained filtering rules for filtering your traffic.
At the top of the page is a list of selectable interfaces.
When a particular interface is selected, details about it is shown in the configuration section.
Where applicable, the configuration is divided into separate sections for source and destination zones.
Add Firewall Rule
If you have networks/devices set up, you can add them to the zone.
To add a device as a zone member:
- Click the Add button
The Select network device dialog opens.
- Open the Select network menu
- Select the device
- Click OK
- Click Apply
Reorder Firewall Rules
Default Firewall Rules
A number of sample firewall rules are enabled by default, providing a basic set of filtering for the network.
Forwarding
Port Forwarding allows remote computers to connect to a specific device within your private network.
The forwarding list shows information about any configured port forwarding rules.
Port Mapping Settings
To map incoming connections:
The port mapping dialog lets you add configuration settings for the mapping.
Ports can be added one by one (80) or as ranges (21:22).
- Add information:
- Add a name as identification
- Add ports:
- Add public/incoming port(s)
- Add private/client port(s)
- Select protocol
- Click Save
- Click Close
Your information is saved and is visible in the mapping list.
Add or Edit Port Mapping
The Add or Edit Port Mapping view allows you to add or change port mapping settings.
| Item | Comment |
|---|---|
| Rule Name | Rule name. |
| Source Zone | Incoming zone. |
| Destination Zone | Destination zone. |
| Source IP Address | Source IP address (for filtering). |
| Dst. Device | Client hostname. |
| Dst. IP Address | Client IP address. |
| Protocol | Mapping protocol (UDP / TCP / TCP + UDP ). |
| Public port(s) | Public (external) port. |
| Private port(s) | Private (client) port. |
| NAT Loopback | Enable NAT Loopback |
Protocol
Add or Edit Port Mapping
The Add or Edit Port Mapping view allows you to add or change port mapping settings.
| Item | Comment |
|---|---|
| Rule Name | Rule name. |
| Source Zone | Incoming zone. |
| Destination Zone | Destination zone. |
| Source IP Address | Source IP address (for filtering). |
| Dst. Device | Client hostname. |
| Dst. IP Address | Client IP address. |
| Protocol | Mapping protocol (UDP / TCP / TCP + UDP ). |
| Public port(s) | Public (external) port. |
| Private port(s) | Private (client) port. |
| NAT Loopback | Enable NAT Loopback |
Protocol
DMZ / Exposed Host
A local network device can be made an Exposed Host. It is placed in the DMZ outside of the firewall, which provides unrestricted Internet access to the network device.
Add Exposed Host
To allow DMZ/exposed host:
- Click Enable to enable an exposed host
- Enter the local IP address to expose
- Alternatively, click select existing host
Note: You should also configure the DMZ IP address as static DHCP address for your device.
Parental Control
Parental control is used to restrict access to the network for particular devices.
Internet Access Scheduling
Parental control is handled by setting schedules where access is restricted to explicitly named MAC addresses.
| Item | Description |
|---|---|
| Weekdays | List of days the filter applies. |
| Start Time | Time of day to start filtering. |
| Stop Time | Time of day to stop filtering. |
| MAC Addresses | List of device MAC addresses. |
Start and Stop Times
The start time for a rule has to be lower than the end time.
If you want to have a rule that goes over midnight, you need to add two rules, one up until midnight, and one from midnight to when you want the rule to end.
For example:
Rule one: From 21:00 To 23:59
Rule two: From 00:00 To 06:00
A single rule of From 21:00 To 06:00 will not be saved.
Quality Of Service
The Quality Of Service view allows you to configure parameters for Quality of Service through applying groups of classes to interfaces.
Interface views
Interface
The interface tab lets you select interfaces and configure Quality of Service profiles for them.
Classification Group
The Classification Group tab lets you manage groupings of QoS classes.
This is useful when you have multiple interfaces and want to manage classes differently for them.
Classify
The classify tab lets you configure filtering parameters in order to define types of traffic to include in which Class.
Workflow
Workflow
In order to use Quality of Service on the traffic for your device, you need to perform a number of configurations.
1: Class
The classes define how network traffic is to be prioritized and allocated.
There are a number of predefined classes, but you can add your own.
2: Classify
In order to direct traffic to the correct classes, you need to define classificaton rules in the Classify tab.
3: Group
With the classes defined, you can add and order them in a class group in the Group tab.
If you have multiple interfaces, and want different QoS settings for them, you can create multiple class groups.
Workflow
In order to use Quality of Service on the traffic for your device, you need to perform a number of configurations.
Process
Configuration steps
The order of operations involved in configuring QoS is different from the order in which the interface displays the setting tabs. Not all settings are needed in all cases.
1: Class
The classes define how network traffic is to be prioritized and allocated.
There are a number of predefined classes, but you can add your own.
2: Classify
In order to direct traffic to the correct classes, you need to define classificaton rules in the Classify tab.
3: Group
With the classes defined, you can add and order them in a class group in the Group tab.
If you have multiple interfaces, and want different QoS settings for them, you can create multiple class groups.
1: Class
The classes define how network traffic is to be prioritized and allocated.
There are a number of predefined classes, but you can add your own.
Predefined Classes
Class
There are a number of predefined classes QoS classes. Each class is a set of definitions for a token bucket.
Default Settings
The predefined classes can be edited and all values changed, but they have default settings that should be suitable in normal cases.
Priority
The priority class is an upstream class for high priority traffic such as handshaking and ICMP packets.
Priority_down
The Priority_down class is an downstream class for high priority traffic.
Express
The Express class is for interactive applications that require bandwidth above standard services so that interactive apps run smoothly.
Normal
The Normal Class is the standard upstream class for all services.
This class will apply to all services not otherwise defined.
Normal_down
The Normal_down class is the standard downstream class for all services.
This class will apply to all services not otherwise defined.
Bulk
The bulk class is suitable for very low priority traffic. It will be allocated available bandwidth if other classes are idle. When other classes are active, it will be allocated bandwidth according to the priority setting.
It is suitable for transfer services such as (P2P and FTP).
Tab
Class
The class tab lets you manage QoS classes.
Overview
At the top of the page is a list of selectable classes.
When a particular class is selected, details about it is shown in the configuration section.
| Item | Description | Comment |
|---|---|---|
| Priority | Bandwidth allocation limit (%). | |
| Average Rate | Average target rate (%). | |
| Limit Rate | Maximum allowed bandwidth (%). | |
| Packet Size | Size of packets (bytes). | See note. |
| Packet Delay | Target delay for packets (ms). | See note. |
| Max Size | Maximum size of packets (bytes). |
Note: Packet Size and Packet Delay rely on the Average Rate setting. The average rate is impacted by the maximum packet delay and the transfer time for the packet size. Generally the delay is lower for smaller packet sizes.
Add Class
You can add as many classes as you like.
To add a class:
- Click the Add button
- Enter a Name for the class
- Enter QoS values as needed.
- Click Apply
Configuration Values
Priority
The Priority indicates the bandwidth allocation limit as a percentage of total available bandwidth.
ls m2 = priority / sum (priority) * max_bandwidth
Limit Rate
The Limit Rate provides a maximum allowed bandwidth, expressed as a percentage of the total available bandwidth.
ul rate = limitrate * max_bandwidth / 100
Average Rate
The Average target rate is a percentage of the total available bandwidth.
Average rate for this class, value in % of bandwidth (this value uses for calculate vaues
'Nx' of 'tc … hfsc rt m1 N1 d N2 m2 N3'
Note: Packet Size and Packet Delay rely on the Average Rate setting. The average rate is impacted by the maximum packet delay and the transfer time for the packet size. Generally the delay is lower for smaller packet sizes.
Packet Size
Size of packets (bytes).
packetsize & packetdelay: (only works if avgrate is present)
rt d = max( packetdelay, 'time required for packetsize to transfer') ls d = rt d
Packet Delay
Target delay for packets (ms).
Max Size
The maximum size of packets indicates the maximum packet size in iptables.
2: Classify
In order to direct traffic to the correct classes, you need to define classificaton rules in the Classify tab.
Tab
Classify
The classify tab lets you configure filtering parameters in order to define types of traffic to include in which Class.
Overview
At the top of the page is a list of selectable classification groups.
When a particular group is selected, details about it is shown in the configuration section.
Adding a parameter will filter out traffic according to the parameters and assign it to the group.
| Item | Description |
|---|---|
| Target | Group to assign. |
| Protocol | Protocol affected (All / UDP / TCP / ICMP). |
| Source Host | (All / Specific host). |
| Destination Host | (All / Specific host). |
| Ports | Included ports anywhere . |
| Source Ports | Included ports in source. |
| Destination Ports | Included ports in destination. |
| Port Range | Range of ports anywhere. |
| Precedence | Precedence. |
| Packet Size | Size of packets to match. |
| Direction | (Both / In / Out) |
| Mark | Hexadecimal mark code to att to the packets. (0x000000-0xFFFFFF) |
| Connbytes | Connection Bytes for when to start filtering. |
| TCP flags | TCP Flags to match. |
Add Filter
To add a filter:
- Click the Add button
- Select Classification group
- Enter QoS values as needed.
- Click Apply
Reorder
3: Group
With the classes defined, you can add and order them in a class group in the Group tab.
If you have multiple interfaces, and want different QoS settings for them, you can create multiple class groups.
Tab
Classification Group
The Classification Group tab lets you manage groupings of QoS classes.
This is useful when you have multiple interfaces and want to manage classes differently for them.
Overview
At the top of the page is a list of selectable classification groups.
When a particular group is selected, details about it is shown in the configuration section.
| Item | Description | Comment |
|---|---|---|
| Default Class | Class to use as fallback if packets don't match any other class. | |
| Classes | Classes to include in the group. | Note: You need to create a class for it to be available in the list. |
The Default Classgroup contains these standard classes: - Priority - Express - Normal - Bulk
Add Classification Group
To add a class group:
- Click the Add button
- Enter a Name for the group
- Select Default group
- Add classes as needed:
- Click Add a new class
- Select the desired class from the list
- Click Apply
4: Enable
As a final step, you enable QoS for the desired interface in the Interface tab.
Tab
Interface
The interface tab lets you select interfaces and configure Quality of Service profiles for them.
Overview
At the top of the page is a list of selectable interfaces.
When a particular interface is selected, details about it is shown in the configuration section.
| Item | Description | ||
|---|---|---|---|
| Enable QoS | Turn the Quality of Service on for the interface. | ||
| Classification Group | Classification group to use for the interface. | Note: You need to create the group for it to be available in the list. | |
| Calculate Overhead | Include overhead in the packet calculations for shaping and policing. | ||
| Limit Download Speed | Restrict the network speed to clients. | ||
| Limit Upload Speed | Restrict the network speed from clients. |
Add Interface
To add an interface:
- Click the Add button
The interface dialog opens.
- Select an Interface from the list
- Click OK
- Enable other settings as needed:
- Turn QoS on with the Enable QoS slider
- Select an available Classification Group
- Turn QoS on with the Limit Download Speed slider
- Enter a speed value (kbps)
- Turn QoS on with the Limit Upload Speed slider
- Enter a speed value (kbps)
- Click Apply
Class
The class tab lets you manage QoS classes.
Overview
At the top of the page is a list of selectable classes.
When a particular class is selected, details about it is shown in the configuration section.
| Item | Description | Comment |
|---|---|---|
| Priority | Bandwidth allocation limit (%). | |
| Average Rate | Average target rate (%). | |
| Limit Rate | Maximum allowed bandwidth (%). | |
| Packet Size | Size of packets (bytes). | See note. |
| Packet Delay | Target delay for packets (ms). | See note. |
| Max Size | Maximum size of packets (bytes). |
Note: Packet Size and Packet Delay rely on the Average Rate setting. The average rate is impacted by the maximum packet delay and the transfer time for the packet size. Generally the delay is lower for smaller packet sizes.
Add Class
You can add as many classes as you like.
To add a class:
- Click the Add button
- Enter a Name for the class
- Enter QoS values as needed.
- Click Apply
Class
There are a number of predefined classes QoS classes. Each class is a set of definitions for a token bucket.
Default Settings
The predefined classes can be edited and all values changed, but they have default settings that should be suitable in normal cases.
Priority
The priority class is an upstream class for high priority traffic such as handshaking and ICMP packets.
Priority_down
The Priority_down class is an downstream class for high priority traffic.
Express
The Express class is for interactive applications that require bandwidth above standard services so that interactive apps run smoothly.
Normal
The Normal Class is the standard upstream class for all services.
This class will apply to all services not otherwise defined.
Normal_down
The Normal_down class is the standard downstream class for all services.
This class will apply to all services not otherwise defined.
Bulk
The bulk class is suitable for very low priority traffic. It will be allocated available bandwidth if other classes are idle. When other classes are active, it will be allocated bandwidth according to the priority setting.
It is suitable for transfer services such as (P2P and FTP).
Interface
The interface tab lets you select interfaces and configure Quality of Service profiles for them.
Overview
At the top of the page is a list of selectable interfaces.
When a particular interface is selected, details about it is shown in the configuration section.
| Item | Description | ||
|---|---|---|---|
| Enable QoS | Turn the Quality of Service on for the interface. | ||
| Classification Group | Classification group to use for the interface. | Note: You need to create the group for it to be available in the list. | |
| Calculate Overhead | Include overhead in the packet calculations for shaping and policing. | ||
| Limit Download Speed | Restrict the network speed to clients. | ||
| Limit Upload Speed | Restrict the network speed from clients. |
Add Interface
To add an interface:
- Click the Add button
The interface dialog opens.
- Select an Interface from the list
- Click OK
- Enable other settings as needed:
- Turn QoS on with the Enable QoS slider
- Select an available Classification Group
- Turn QoS on with the Limit Download Speed slider
- Enter a speed value (kbps)
- Turn QoS on with the Limit Upload Speed slider
- Enter a speed value (kbps)
- Click Apply
Classification Group
The Classification Group tab lets you manage groupings of QoS classes.
This is useful when you have multiple interfaces and want to manage classes differently for them.
Overview
At the top of the page is a list of selectable classification groups.
When a particular group is selected, details about it is shown in the configuration section.
| Item | Description | Comment |
|---|---|---|
| Default Class | Class to use as fallback if packets don't match any other class. | |
| Classes | Classes to include in the group. | Note: You need to create a class for it to be available in the list. |
The Default Classgroup contains these standard classes: - Priority - Express - Normal - Bulk
Add Classification Group
To add a class group:
- Click the Add button
- Enter a Name for the group
- Select Default group
- Add classes as needed:
- Click Add a new class
- Select the desired class from the list
- Click Apply
Classify
The classify tab lets you configure filtering parameters in order to define types of traffic to include in which Class.
Overview
At the top of the page is a list of selectable classification groups.
When a particular group is selected, details about it is shown in the configuration section.
Adding a parameter will filter out traffic according to the parameters and assign it to the group.
| Item | Description |
|---|---|
| Target | Group to assign. |
| Protocol | Protocol affected (All / UDP / TCP / ICMP). |
| Source Host | (All / Specific host). |
| Destination Host | (All / Specific host). |
| Ports | Included ports anywhere . |
| Source Ports | Included ports in source. |
| Destination Ports | Included ports in destination. |
| Port Range | Range of ports anywhere. |
| Precedence | Precedence. |
| Packet Size | Size of packets to match. |
| Direction | (Both / In / Out) |
| Mark | Hexadecimal mark code to att to the packets. (0x000000-0xFFFFFF) |
| Connbytes | Connection Bytes for when to start filtering. |
| TCP flags | TCP Flags to match. |
Add Filter
To add a filter:
- Click the Add button
- Select Classification group
- Enter QoS values as needed.
- Click Apply
Reorder
MultiWAN
The MultiWAN view allows you to create and configure WAN traffic divisions for load balancing and failover and apply traffic rules.
The MultiWAN settings are divided into tabs.
MultiWAN Settings
The MultiWAN Settings tab allows you to turn MultiWAN feature on or off, and configure Mutiple WAN connections.
Traffic Rules
The Traffic Rules tab allows you to filter LAN traffic and assign it to the appropriate WAN.
MultiWAN Settings
The MultiWAN Settings tab allows you to turn MultiWAN feature on or off, and configure Mutiple WAN connections.
Below the general settings is a list of selectable WANs.
When a particular WAN is selected, details about it is shown in the configuration section.
| Item | Description |
|---|---|
| Load Balancer Distribution | Disable / 1-10 (only used in balancer mode. |
| Health Monitor Method | Ping / Statistics. |
| Health Monitor Interval | Time between health checks. |
| Health Monitor ICMP Host(s) | ICMP host. |
| Health Monitor ICMP Timeout | ICMP timeout. |
| Attempts Before WAN Failover | Number of connection attempts before switching to failover WAN. |
| Attempts Before WAN Recovery | Number of connection attempts before attempting to recover WAN. |
| Failover Traffic Destination | Destination for traffic in case of failover. (Fast/ Load). |
| DNS Server(s) | Specified DNS / Automatic Selection / Customized DNS |
Add WAN
You can add as many WANS as you have WAN connections.
To add a WAN:
- Click the Add button
- Select an available WAN
A new WAN is added to the list.
- Edit the parameters as needed.
- Click Apply
Add Custom DNS Servers
Traffic Rules
The Traffic Rules tab allows you to filter LAN traffic and assign it to the appropriate WAN.
At the top of the page is a list of rules.
When a particular rule is selected, details about it is shown in the configuration section.
Add Rule
You can add as many rules as you like.
To add a rule:
- Click the Add button
A new rule is added to the list.
- Edit the parameters as needed.
- Click Apply
MultiWAN Options
Some aspects of MultiWan configuration require a bit of thinking and decisions.
Sample Configurations
Example configurations for failover and balancer are available from the OpenWRT site
Load Balancer Weights
You can add any number of servers to a server load balancing action. You can also add a weight to each server to make sure that your most powerful servers are given the heaviest load.
The weight refers to the proportion of load that the XTM device sends to a server. By default, each server has a weight of 1.
If you assign a weight of 2 to a server, you double the number of sessions that the XTM device sends to that server, compared to a server with a weight of 1.
Load Balancing Interfaces
If an interface is not specified for some particular traffic - and metric and weight are the same - the default behavior is to use both interfaces, which is the Linux default load sharing mechanism.
Interface Selection
When selecting which interface weights you need to take into account how the operator handles traffic. For example, usually a fiber or DSL WAN connection should have higher weight than a mobile connection.
Health Monitor Ping / Statistics
-Health Monitor Method Ping / Statistics. Ping I understand. What kind of statistics are used? Where can one configure statistcs limits? E.g if you monitor like wan stats when does the box determine that interface has failed ? No stats at all at some interval? Some stats in some interval but it doesn’t trigger wan failover because…..?
Ping and Statistics are health monitor methods.
Statistics checks the rx bytes value with the Health Monitor Interval, and if the value has not changed it marks the link as unhealthy.
Failover Traffic Destination
Failover is used when the original link is not available. It is needed both when using a specified interface or when using a balancing mechanism.
When selecting the Failover Traffic Destination, you can choose between Load Balancer, Fast Balancer or using a specific interface. Fast balancer uses netfilter iptables and load balancer uses iproute2.
Services
The Services view allows you to configure the services connected device.
Printer Server
The Printer Server Settings view allows you to change different features about your printer server for connected printers.
Printer Server
The Printer Server Settings view allows you to change different features about your printer server for connected printers.
| Item | Comment |
|---|---|
| Enable | Turn printer server on or off. |
| Interface | Interface to listen on |
| Port | Port to listen on. |
| Bidirectional mode | Allow printer to communicate with client. |
MiniDLNA
The MiniDLNA view lets you configure the MiniDLNA server.
Status
At the top of the page is a status window that can be expanded to display the current MiniDLNA status.
General
In the General settings tab you can change different general features about your MiniDLNA server.
Status
At the top of the page is a status window that can be expanded to display the current MiniDLNA status.
Show Status
To view the status window, click the expand icon.
Media Library
In the media library table, the number of audio, video and image files on the server is shown.
Connected Clients
The Connected Clients table displays information about possible clients and their connections to the server.
General
In the General settings tab you can change different general features about your MiniDLNA server.
| Item | Comment |
|---|---|
| Port | Port for HTTP traffic. |
| Network | List of interfaces to serve. |
| Friendly Name | Name to display to clients. |
| Root Container | Start point when browsing. |
| Media Directories | File system locations for media. |
| Album-Art Names | List of file names for album art. |
Advanced
In the Advanced tab you can change different advanced features about your media server.
| Item | Comment |
|---|---|
| Database directory | Directory for database and cache storage. |
| Log directory | Directory to store logs. |
| Enable inotify | Turn Inotify on or off. |
| Enable TIVO | Support for streaming files to TiVo. |
| Strict to DLNA standard | Only use DLNA standard features. |
| Presentation URL | Default presentation URL. |
| Notify interval | Time between notification messages. |
| Announced serial number | Serial number to show to clients. |
| Announced model number | Model number to report to clients. |
| miniSSDP socket | Path to miniSSDPd socket for SSDP. |
UPnP
The UPNP view allows you to configure UPNP services.
At the top of the page is a list of currently open UPnP ports, if any.
The UPnP settings are divided into tabs.
General
The General tab allows you to enable and configure the service parameters.
| Automatically Start Service At Bootup | Enable upnp daemon at boot time |
| Start / Stop Service | Start/stop upnp daemon. |
| Enable UPNP | Enable UPNP protocol |
| Enable NAT-PMP | Enable NAT-PMP protocol. |
| Enable secure mode | Only add forwards to requesting ip addresses. |
| Enable additional logging | Aadd extra debugging information to the system log. |
| Downlink | Nominal uplink speed (KByte/s). |
| Uplink | Nominal downlink speed (KByte/s). |
| Port | Port for the service. |
| External Interface | Interface for external access. |
| Internal Interface | Interface to use for local access. |
Advanced
The Advanced tab lets you configure advanced UPNP settings.
| Device UUID | UUID |
| Announced serial number | Serial number to show to clients. |
| Announced model number | Model number to show to clients. |
| Notify interval | Time between notification messages. |
| Clean rules threshold | Number of rules to keep. |
| Clean rules interval | Time between cleaning of UPnP rules. |
| Presentation URL | Location for service control web interface. |
| UPnP lease file | Location for file containing leases. |
DDNS
The DDNS view allows you configure Dynamic DNS services for your device.
At the top of the page is a list of selectable services.
When a particular service is selected, details about it is shown in the connection section.
| Item | Description |
|---|---|
| Enabled | Turn service on or off. |
| Label | Identifier in the service list. |
| IP Retrieval Method | Interface / Network / Script / Web. |
| Select Interface | For Interface: Interface. |
| Select Connection | For Network: Connection. |
| Script Path | For Script: Local path to IP detection script. |
| Enter website to poll for ip address | For Web: Address to IP detection service. |
| Provider | Service provider list. |
| Enter DDNS Provider | Manually add service provider. |
| Domain name | Full hostname to use for the device. |
| Username | Service account username. |
| Password | Service account password. |
| Use HTTPS | USe secure communication with service. |
DDNS Services
You can add as many DDNS Services as you like.
To add a DDNS Service:
- Click the add button
A new service is added to the list.
- Edit the parameters as needed.
- Click Apply
IPTV
The IPTV view lets you configure the IPTV server.
| Item | Description |
|---|---|
| Differentiated Services Code Point | DSCP to use for tagging outgoing IGMP packets. |
| Proxy interface | Interface to use as proxy. |
| Default version | IGMP version. |
| Query interval | Time between IGMP query messages. |
| Query response interval | Time to wait for response to query beofre timeout. |
| Last member query interval | Time between queries to determine the loss of the last member in an IGMP group. |
| Robustness value | Tolerance for lost packets. |
| LAN to LAN multicast | Allow multicast between LANs. |
| Max groups | Maximum allowed multicastgroups. |
| Max sources | Maximum allowed multicast sources. |
| Max members | Maximum allowed members in a multicast group. |
| Fast leave | Leave multicast groups immediately after the last host. |
| Join immediate | Join group directly. |
| Enable IGMP proxy | Turn on IGMP Proxy handling. |
| Ignore SSM Range | Ignore SSM and deliver regular multicasting. |
| IGMP snooping mode | IGMP snooping mode: Disabled / Standard / Blocking. |
| IGMP snooping interfaces | Interfaces to use for IGMP snooping. |
DHCP
The DHCP view lets you configure the DHCP server settings.
The DHCP settings are divided into several tabs.
Classifications
The Classifications tab lets you add classifications for connected clients.
The classifications can be used to provide specific DHCP Options options for the classified clients, based on client parameters.
General
The General tab allows you to configure the DHCP server basic settings.
| Item | Description |
|---|---|
| Local domain | Local domain suffix appended to DHCP names and hosts file entries. |
| Log queries | Write received DNS requests to system log. |
| Leasefile | file where given DHCP leases will be stored. |
| Ignore resolve file | Do not use the local Resolve file. |
| Resolve file | Local DNS file storage. |
| Ignore Hosts file | Do not use the local Hosts file. . |
| Hostname Entries file(s) | Path to additional host files to read for serving DNS responses. |
Advanced
The Advanced tab allows you to configure advanced settings for the DHCP server.
| Item | Description |
|---|---|
| Domain required | Do not forward DHCP-requests without DHCP-Name. |
| Authoritative | This is the only DHCP in the local network. |
| Filter private | Do not forward reverse lookups for local networks. |
| Filter useless | Do not forward requests that cannot be answered by public name servers. |
| Localise queries | Localise hostname depending on the requesting subnet if multiple IPs are available. |
| Local server | Domain resolved from DHCP or hosts files only. |
| Expand hosts | Add local domain suffix to names served from hosts files. |
| No negative cache | Do not cache negative replies. |
| Strict order | DHCP servers will be queried in the order of the resolvfile. |
| Bogus NX Domain Override | List of hosts that do not supply non-existent domain (NXDOMAIN) results. |
| DHCP forwarding | List of DHCP servers to forward requests to. |
| Rebind protection | Discard upstream RFC1918 responses. |
| Allow localhost | Allow upstream responses in the 127.0.0.0/8 range. |
| Domain whitelist | List of domains to allow RFC1918 responses to. |
| DHCP server port | Listening port for inbound DHCP queries. |
| DHCP query port | Fixed source port for outbound DHCP queries. |
| Max DHCP leases | Maximum allowed number of active DHCP leases. |
| Max. EDNS0 packet size | Maximum size of EDNS0 UDP packets. |
| Max. concurrent queries | Maximum number of concurrent DHCP queries. |
Classifications
The Classifications tab lets you add classifications for connected clients.
The classifications can be used to provide specific DHCP Options options for the classified clients, based on client parameters.
Parameters
The classification can be based on client parameters:
- MAC class
View
At the top of the page is a list of configured classifications.
When a particular account is selected, details about it is shown in the configuration section.
For all classification types, the configuration is similar:
| Item | Description |
|---|---|
| Parameter value | Value for the classification parameter, according to its type. |
| Network ID | Option value. |
| ID | DHCP option ID. |
| Option | Option value. |
Add Tag
You can add as many tags as you like.
To add a tag:
- Click the Add button
The Select type of Classification dialog opens:
- Pick a Select Classification Type from the dropdown menu
- Click Apply
The tag is added to the list.
- Click the Edit button
- Enter Parameter value according to Classification Type
- Add as many DHCP options as needed:
- Click the Add option button
- Select the ID value
- Enter Option value
- Click Apply
Hostnames
The Hostname tab allows you to configure hostnames for IPv4 or IPV6 addresses in the LAN.
| Item | Description |
|---|---|
| Hostname | List of hostnames. |
| Family | Type of IP address (IPv4 or IPv6). |
| Address | IPv4 or IPv6 address. |
Add Hostname Entry
You can add as many entries as you like, and each entry can have any number of hostnames for each IP address.
To add a hostname entry:
- Click the Add button
- Enter hostnames in the Hostname field
- Select address Family
- Enter IP Adress to redirect to
- Click Apply
SNMP
The SNMP Configuration view lets you configure the Simple Network Management Protocol service.
The SNMP settings are divided into tabs.
System
The System tab lets you configure general information about the SNMP service.
| Item | Description |
|---|---|
| Location | Physical location of the device. |
| Contact | Contact information for the responsible person. |
| Name | Name of the server. |
| Services | Offered services. |
| Description | Server description for presentation. |
| Object ID | Identifier for the device. |
Agent
The Agent tab allows you to manage SNMP agents.
| Item | Description |
|---|---|
| Agent Address | Protocol and port for the agent variable. |
Add Agent
You can add as many agents as you like.
To add an agent:
- Click the Add button
- Enter an Agent Address
- Click Apply
Com2Sec
The Com2Sec tab lets you configure Com2Sec access profiles for the SNMP service.
| Item | Description | Example |
|---|---|---|
| Community | Community group to access. | private |
| Source | Hostname or subnet. | localhost |
| SecName | Access string. | rw |
Add Profile
You can add as many profiles as you like.
To add a profile:
- Click the Add button
- Enter parameters as needed
- Click Apply
Group
The Group tab allows you to configure Com2Sec access groups for the SNMP service.
| Item | Description | Example |
|---|---|---|
| Community | Community group to access. | public |
| Source | Hostname or subnet. | usm |
| SecName | Access string. | ro |
Add Group
You can add as many groups as you like.
To add a group:
- Click the Add button
- Enter parameters as needed
- Click Apply
View
The View tab lets you configure Com2Sec views for the SNMP service.
| Item | Description |
|---|---|
| View Name | Name of the view. |
| Type | Type of view. |
| OID | Object ID |
| Mask | Netmask. |
Add View
You can add as many views as you like.
To add a view:
- Click the Add button
- Enter parameters as needed
- Click Apply
Access
The Access tab allows you to configure Com2Sec access directives for the SNMP service.
The access directive maps from group/security model/security level to a view.
| Item | Description | Example |
|---|---|---|
| Group | Group. | |
| Context | Security name or empty. | |
| Version | Version access. | any / v1 / v2c / usm |
| Level | Access level. | noauth / auth / priv |
| Prefix | Context matching. | exact / prefix |
| Read | Read permissions | |
| Write | Write permissions | |
| Notify | Notify permissions. |
Add Access Group
You can add as many acces groups as you like.
To add a n accwess group:
- Click the Add button
- Enter parameters as needed
- Click Apply
Pass
| Item | Description |
|---|---|
| Persist | Enable permanent passthrough. |
| Priority | Passthrough priority. |
| MIB OID | Object ID for the MIB. |
| Program | Execution for the arguments. |
Add Passthrough
You can add as many passthroughs as you like.
To add a passthrough:
- Click the Add button
- Enter parameters as needed
- Click Apply
Samba
In the Samba view you can change settings for the Sambaserver.
The Samba settings are divided into sections.
General
The General section of the view allows you to change the general Samba settings, such as name, workgroup and interface.
General
The General section of the view allows you to change the general Samba settings, such as name, workgroup and interface.
| Option | Description |
|---|---|
| Name | Service identifier. |
| Workgroup | Service workgroup. |
| Description | Description of the service. |
| Interface | Interfaces to provide the service to. |
Change Interface Settings
To change the interface that Samba will listen on:
- Click LAN to open the list
- Choose as many interfaces as needed
- Click outside of the list
- Click Apply
Samba Users
The Samba Users section of the view allows you to change the user settings.
| Option | Description |
|---|---|
| Username | user name |
| Password | password |
| Description | description |
Samba User Settings
To add a Samba user:
- Click Add
- Edit the parameters as needed.
- Click Apply
WIFI
The WiFi view shows you information about your wireless network.
Band Steering
The Band Steering view allows you to enable and configure band steering for the device.
WPS Settings
The WPS Settings view lets you change the default wireless security settings (WPS) to make your network more secure.
MAC Filter
In the MAC Filter view you can make your wireless network more secure. Just specify which devices are allowed to connect, or explicitly lock out devices.
General
In the General WiFi view you can view and edit the wireless interface.
Wireless
In the Wireless view you can view and edit the wireless interfaces.
Each radio can have up to 4 SSIDs.
Radios
The Wireless Radios view allows you to configure wireless radios installed on your system.
At the top of the page is a list of radios.
Clicking the Edit buttin will open the edit view for that radio.
| Item | Comment |
|---|---|
| Radio On/off | Turn radio on or off. |
| WiFi Mode (SSID) | Choose wifi mode. |
| Channel | Choose WiFi Channel. |
| Bandwidth | Choose bandwidth. |
| Scan Timer | Determine the dwell time for channel hopping. |
| DFS Channels | Turn DFS channels on or off. |
| Beamforming | Turn beamforming on or off. |
| Airtime Fairness | Turn ATF on or off. |
| Maximum Associated Stations | Maximum number of clients allowed. |
| RX Chain PowerSave Quiet Time | Turn RXC PS Quiet Time on or off. |
| RX Chain PowerSave PPS | Turn RXC PS PPS on or off one of the receive chains to save power. |
| Enable WMM Multimedia Extensions | Turn WMM multimedia extensions on or off. |
| Disable WMM Ack | Turn WMM acknowledgement on or off. |
| Enable WMM UAPSD Power Saving | Turn WMM UAPSD power saving on or off. |
Wireless
In the Wireless view you can view and edit the wireless interfaces.
Each radio can have up to 4 SSIDs.
At the top of the page is a list of selectable interfaces.
When a interface is selected, the edit view for the interface is shown below.
| Item | Comment |
|---|---|
| Enabled | Turn on or off. |
| WiFi Network Name | Edit name of SSID network. |
| Broadcast SSID | Toggle to make network visible or invisible. |
| Wireless Multicast Forwarding | Toggle to turn multicast forwarding on or off. |
| Maximum Number of Connected Clients | Maximum number of connected clients. |
| Encryption | Change to a different encryption method. |
| Cipher | Choose form of Cipher. |
| WiFi Key (Password) | Reset to default password. |
| Show Key Text | Change format of wifi key text. |
Add Wireless Interface
Band Steering
The Band Steering view allows you to enable and configure band steering for the device.
| Item | Comment |
|---|---|
| Enable | Turn band steering on or off. |
| Steering Policy | RSSI or bandwidth. |
| Threshold | Bandwidth or RSSI threshold value. |
Enable Band Steering
To enable band steering:
- Click Enable toggle
- Choose steering policy
- Set threshold value to use for the selected policy.
WPS Settings
The WPS Settings view lets you change the default wireless security settings (WPS) to make your network more secure.
General WPS Settings
The WPS Settings section allows you to choose and configure different connection methods on an encrypted channel.
WPS-PBC: Push Button on Device
The WPS-PBC: Push Button on Device section lets you pair your devices.
WPS/REG: Device provides PIN
The section WPS-REG: Device provides PIN lets you generate a personal identification number through WPS.
WPS-PIN: Another Device provides PIN
The section WPS-PIN: Another Device provides PIN allows you to enter a PIN provided by another device.
General WPS Settings
The WPS Settings section allows you to choose and configure different connection methods on an encrypted channel.
| Item | Comment |
|---|---|
| WPS Function | Turn on or off for device. |
| Enable WPS on (5GHz) | Turn WPS on or off for radio. |
| Enable WPS on (2.4GHz) | Turn WPS on or off for radio. |
WPS-PBC: Push Button on Device
The WPS-PBC: Push Button on Device section lets you pair your devices.
| Item | Comment |
|---|---|
| Enable WPS button on device | Turn on or off. |
| Pressing WiFi on/off button on your device for long time activates pairing | Turn on or off. |
| Pair (within 2 minutes) | Pair button. |
Pairing Your Device
To a device via WPS:
- Click the Pair button
- Press the corresponding button on the device you wish to connect
Your device will be open for pairing for two minutes.
WPS-PIN: Another Device provides PIN
The section WPS-PIN: Another Device provides PIN allows you to enter a PIN provided by another device.
| Item | Comment |
|---|---|
| Enter your device PIN | Enter device PIN |
| Pair (within 2 minutes) | Pair button. |
WPS/REG: Device provides PIN
The section WPS-REG: Device provides PIN lets you generate a personal identification number through WPS.
| Item | Comment |
|---|---|
| WPS Using Generated PIN | Turn on or off. |
| Generated PIN | Generated PIN shown |
| Generate PIN | Generate button. |
Generating a PIN
To generate a PIN through WPS:
- Click the Generate button
MAC Filter
In the MAC Filter view you can make your wireless network more secure. Just specify which devices are allowed to connect, or explicitly lock out devices.
Filters can be applied separately for each radio .
The devices are identified by their MAC address. You can manage up to 32 devices.
| Section | Description |
|---|---|
| MAC Filtering | Turn filtering on or off. |
| Access for listed devices | Access setting for clients in the list. |
| Currently added devices | List of filtered devices. |
| Add currently connected hosts ot the list | Collect all currently active devices to the list. |
Enable MAC Filter
System
The System view provides access to device information, management, provisioning and settings.
General Settings
The General Settings view contains basic device settings.
| Item | Description |
|---|---|
| Local Time | Local time for the device. |
| Timezone | Device timezone setting. |
| Hostname | Device hostname. |
Firmware Upgrade
The Firmware Upgrade view lets you upgrade the device firmware by using image files.
IUP
The IUP view allows you to set up parameters for provisioning services and configurations with Inteno Universal Provisioning.
TR69
The TR69 Settings view allows you to configure TR069 support for device management and provisioning from the WAN.
Power Management
The Power Management view allows you to manage CPU effiency and Ethernet hardware ports.
General Settings
The General Settings view contains basic device settings.
| Item | Description |
|---|---|
| Local Time | Local time for the device. |
| Timezone | Device timezone setting. |
| Hostname | Device hostname. |
Time Servers
The Time Servers section shows NTP time servers in use.
| Item | Description |
|---|---|
| Time Servers (NTP) | List of NTP servers to use. |
| Server Mode | Turn NTP server mode on or off. |
Add Server
Log Settings
The Log Settings view contains settings for the system logs.
Current Firmware
| Item | Description |
|---|---|
| System Log Level | System Logging level |
| Cron Log Level | Cron Logging level |
| Kernel Log Level | Kernel Logging level |
| Log File | Location to save the log file. |
| Log IP | IP address of remote log server. |
| Log Port | Port for the remote log server. |
| Log Prefix | Prefix to use in log. |
| Log Protocol | Protocol for transfer of log information (UDP / TCP). |
| Log Remote | Turn remote logging on or off. |
| Log Size | Max size of log in Kb. |
| Trailing null | Use trailing null insted of newline when using TCP |
| Log Type | Type of logging to use (circular = limited /file = unlimited number of files). |
Connectivity Test
The Connectivity Test view allows for automatic verification of the Internet connection by accessing a predefined URL.
Current Firmware
| Item | Description |
|---|---|
| Internet | URL for checking Internet connection. |
Passwords
The Passwords view lets you change passwords for device users.
Change Password Dialog
| Item | Description |
|---|---|
| Current Password | The existing password. |
| New Password | Password to change to. |
| Reenter Password | Verification of new password. |
| Password Strength | Indicates the security level of the new password. |
Note: For security reasons, the current password is never displayed.
Change password
To change password for a user:
- Open the Change password for user
- Select a user role
- Click Change Password
The change password dialog opens.
- Enter the current password
- Enter the new password
- Enter the new password again
- Click Change Password
Firmware Upgrade
The Firmware Upgrade view lets you upgrade the device firmware by using image files.
Current Firmware
The Current Firmware Version shows currently installed firmware on the device.
USB Firmware Upgrade
In the USB Firmware Upgrade section you can perform an automatic search for upgrade image file on USB devices, and perform the upgrade.
The check for upgrade starts a search for image files on any connected USB devices.
Note: The type of image file to use for upgrades is defined in Firmware options.
Manual Firmware Upgrade
In the manual firmware upgrade section you can select an image file on your computer, upload it to the device, and perform the upgrade.
| Item | Description |
|---|---|
| Select firmware file to upload | Upgrade image file on local computer. |
| Start upgrade | Button to start upgrade. |
Backup/Restore
The Backup/Restore view allows you to manage backups and resets of the device.
Backup Settings
In the Backup Settings section you can save a copy of your device configuration or load a saved configuration into the device.
Save Backup
- Click Save
The Save Configuration dialog opens.
- If you want to encrypt the backup file:
- Enter a Backup file password
- Retype the password
- Click Continue
The file is saved as a compressed file archive to your local computer.
Load Backup
To load a saved configuration the factory reset:
- Click Load
- Click Continue
The Load New Configuration dialog opens.
- Click Choose File
- If the backup file is encrypted:
- Enter a Backup file password
Factory Settings
In the Factory Settings you can
Note: Reset restores your device to the factory defaults and remove any configurations ou have made.
To perform the factory reset:
- Click Reset
Backup Settings
The Backup Settings view lets you select which services and settings to include in backups.
The list contains a selection of services and settings that can be included when performing backups.
You can change the status of any item by moving the associated slider.
IUP
The IUP view allows you to set up parameters for provisioning services and configurations with Inteno Universal Provisioning.
The IUP view is divided inte several sections.
General
In the General section you can manage general provisioning settings.
| Item | Description |
|---|---|
| Enabled | Turn provisioning on or off. |
| Update interval start time | Time of day to start update. |
| Update interval | Hourly / Daily / Weekly. |
| Export file | Download provisioning file. |
Main Provisioning Server
In the Main Provisioning Server section you can add a manual provisioning server address.
Note: This will override DHCP Discover Provisioning, even if it is enabled.
| Item | Description |
|---|---|
| Enabled | Turn main provisioning server on or off. |
| Reboot | Reboot after configuration has been applied. |
| URL | Address to the provisioning server. |
| Decryption Key | Key for encrypted provisioning archive. |
DHCP Discover Provisioning Server
In the DHCP Discover Provisioning Server section you can enable automatic discovery of provisioning server.
| Item | Description |
|---|---|
| Enabled | Turn software update on or off. |
Software Update Config
In the Software Update Config section you can configure online update of software.
| Item | Description |
|---|---|
| Enabled | Turn software update on or off. |
| Item | Description |
|---|---|
| Enabled | Turn software update on or off. |
| Default reset | Remove device configurations and set to default. |
| Software URL | Location of software configuration. |
Sub Configs
In the sub configs section you can add sub configurations of specific parts.
| Item | Description |
|---|---|
| URL | Location of configuration file. |
| Package Control | |
| Enabled | Turn sub configurations on or off. |
Add Sub Config
To add a sub configuration:
- Click Add sub config
- Enter the URL for the configuration file
- Enter the relevant Package Control
- Select if the su config should be Enabled
TR69
The TR69 Settings view allows you to configure TR069 support for device management and provisioning from the WAN.
The TR69 view is divided into sections.
Configure ACS Specific Settings
In the ACS section, you can configure ACS settings.
| Item | Description |
|---|---|
| ACS User Name | USer name for the ACS connection. |
| ACS Password | Password for the ACS connection. |
| URL | Location of the ACS server. |
| Periodic Inform Enable | Turn Periodic Inform on or off. |
| Periodic Inform Time | Absolute UTC time when CPEs will send Periodic Inform calls. |
| DHCP Discovery | Turn automatic discovery of server on or off. |
Configure CPE Specific Settings
In the CPE section, you can configure CPE connection settings.
| Item | Description |
|---|---|
| WAN Interface | Interface for the connection. |
| Connection Request User Name | User name for the ACS connection |
| Connection Request Password | Password for the ACS connection. |
| Port | Specific connection port. |
| Log Severity Level | Logging information level. |
| Log to console | Display logging messages in the console. |
| Log to file | Turn logging to file on or off. |
| Log file max size | Size of log file. |
| Provisioning Code | Identifier for provisioning. |
OWSD
The OWSD view lets you configure settings for the open web-server daemon.
The server listens on a number of interfaces, and allows for separate configuration of access for each of them.
At the top of the page is a list of interfaces the server listens on.
When a particular interface is selected, details about it is shown in the configuration section.
Configuration
The Configure firewall rule section allows you to enable and configure a firewall rule for the selected service.
Add Listen Interface
- Click Add
- Enter a Name
The firewall settings are displayed.
- Add interface settings as needed.
- Click Apply
Add Origin
Select an interface in the list.
- Click Add
- Enter the Origin
- Click Add
- Click Apply
SSH
The SSH view allows you to configure SSH access, server instances, and keys.
General Settings
The General Settings section contains management options for the SSH service.
| Item | Description |
|---|---|
| Enabled | Turn SSH on or off. |
| Verbose Logging | Turn verbose logging on or off. |
Dropbear Instances
The Dropbear Instances section lets you create SSH server instances with different parameters.
| Item | Description |
|---|---|
| Password Autentication | Turn access with password authentication on or off. |
| Port | Connection port. |
| Enable Root Password Auth | Turn root access with password authentication on or off. |
| Enable Root Login | Turn root account access on or off. |
| Enable Forwarded Ports | Turn forwarded ports on or off. |
| Interface | Restrict SSH server to particular interface. |
Add SSH Server instance:
To add a SSH Server instance:
- Click Add
- Enter parameters for the instance
- Click Apply
Accepted SSH Keys
The SSH view allows you to configure SSH access, server instances, and keys.
To add a SSH key:
- Click Add
- Copy the public SSH key
- Paste the public SSH key into the window
- Click OK
- Click Apply
Services
The Services view lets you configure WAN access to device services.
Allow WAN Access To Running Services
At the top of the page is a list of services.
When a particular service is selected, details about it is shown in the configuration section.
Configure firewall rule for this service
The Configure firewall rule section allows you to enable and configure a firewall rule for the selected service.
Where applicable, the configuration is divided into separate sections for source and destination zones.
| Item | Description |
|---|---|
| Enable WAN forwarding for this service | Turn WAN access on or off. |
| Name | Identifier for the rule. |
| Zone | Device / Any / LAN / WAN |
| IP | IPv4 / IPv6 address. |
| MAC | MAC address. |
| Port | Port affected. |
| IP version | Any / IPv4 / IPv6 |
| Protocol | Protocol affected: (UDP / TCP / ICMP / TCP + UDP / ESP) |
| Firewall action | Firewall action to perform. |
Add Firewall Rule
Select a service in the list.
- Click the Enable WAN forwarding for this service button
The firewall settings are displayed.
- Add rule settings as needed.
- Click Apply
LEDs
The LED view allows you to enable or disable the status LEDs on your device.
Displayed Leds
The exact LEDs available vary with device type. The status of each LED is shown on the left of the name.
Examples
BROADBAND
DECT
DSL
EXT
INTERNET
LOGO
STATUS
VOICE1
WAN
WIFI
WPS
Toggle LED
To switch a LED on or off:
- Find the desired LED in the list
- Click the slider button in the interface
- Click Apply
Power Management
The Power Management view allows you to manage CPU effiency and Ethernet hardware ports.
| Item | Description |
|---|---|
| CPU Speed | CPU Sync. |
| CPU r4k Wait | Sleep mode configuration. |
| Ethernet Auto Power Down | Turn Ethernet Auto Power Down on or off. |
| Energy Efficent Ethernet | Turn Energy-Efficient Ethernet on or off. |
Services
The Services view lets you manage system services on the device.
The list contains system running and available services.
| Item | Description |
|---|---|
| Priority | System priority. |
| Service | Service identifier. |
| Enable | Enable or disable service. |
| Action | Buttons to start, stop and restart the service. |
Restart
The Restart page allows to restart your Internet connection and reboot your device.
Restart device
Note: Restarting the device will disconnect all phone, Internet and TV services while the device is restarting.
To restart your device:
- Click Restart
A confirmation dialog is shown
- Click Yes
A restart dialog is shown.
When the device has restarted, the browser reconnects and the login dialog is shown.
Status
The Status area provides an overview of the current situation for your device, network and services, and also contains diagnostic tools.
System
The System Status view displays information about a number of parameters regarding your gateway and its operation.
IGPM TV
The IGPM TV Status views shows information about your IPTV services and their connection status.
WiFi
The WiFi Status view shows information about the wireless network, and allows you to scan the local area for other wireless access points.
USB
The USB devices views displays information about any USB devices connected to the gateway device.
Note: Supported file systems for USB devices are NTFS and FAT32.
Voice
The Voice Status view shows information about SIP accounts, phone numbers and voice lines connected to the device.
System
The System Status view displays information about a number of parameters regarding your gateway and its operation.
System
The System Status overview shows basic data about the device.
Configuration
| Option | Description | Sample value | |
|---|---|---|---|
| Hostname | The hostname for the gateway. | Inteno | |
| Model | Gateway model. | DG400A | |
| Firmware Version | Version of installed firmware. | DG400-WU7UINT3.5.5-1605131617 | |
| Kernel Version | The gateway operating system kernel version. | 3.11 | |
| Filesystem | Filesystem used in gateway storage. | UBIFS | |
| BRCM Version | (Broadcom Devices only) Version number for the Broadcom driver. | 4.16L.04 | |
| Local Time | Time according to the gateway internal clock. | Mon May 23 2016 17:21:12 GMT+0200 (CEST) | |
| Uptime | Time the gateway has been runnning since last startup. | 5d 2h 53m 14s | |
| CPU | Percentage of CPU processing in use. | 0% | |
| Active Connections | Number and percentage of connections to the gateway. | 259 / 7660 (3%) |
System Memory
The System Memory Status view displays information about memory usage in the device.
Configuration
| Option | Description | Sample value |
|---|---|---|
| Usage | Memory used by the system. | 163144 kB / 226308 kB (72%) |
| Shared | Shared memory in use. | 0 kB / 226308 kB (0%) |
| Buffered | Memory buffer in use. | 0 kB / 226308 kB (0%) |
| Swap | Swap file system used. | 0 kB / 0 kB (0%) |
System Storage
The System Storage Status view shows information about file systems and space used.
Examples
| Option | Description |
|---|---|
| rootfs(/) | Root. |
| tmpfs(/tmp) | Temporary. |
| tmpfs(/dev) | Devices. |
| tmpfs(/mnt) | Mount point. |
| tmpfs(/dev/sda1) | An attached USB stick. |
Processes
The Processes view shows information about system processes and CPU usage.
Overview
The overview shows a summary of the processes:
| Item | Description | Comment |
|---|---|---|
| Total number of processes | 96 | |
| Total CPU usage | 9% |
Process Detail Toggle
You can access detailed realtime information about running processes, by clicking the information toggle.
To open the Details view:
- Click Click here to view details
Details
In the details view, you can get detailed information about all processes running on the device.
Configuration
For each process, information about a number of properties is displayed:
| Property | Description | Comment |
|---|---|---|
| PID | Process ID | Unique identifier for the process. |
| PPID | Parent Process ID | Unique identifier for the parent process. |
| USER | User running the service. | |
| STAT | State Code. | |
| VSZ | Virtual Memory Size. | |
| %VSZ | Virtual Memory Size Percentage. | |
| %CPU | CPU Percentage. | |
| COMMAND | The command used to run the process. |
Network
The Network Status view shows information about various aspects of your network.
Routing
The Routing Status view shows the static routes configuration for the various network types.
Status
The Network Status view provides an overview of network elements for your device.
WAN6
The WAN6 view shows information about any connected IPv6 network.
LAN
The LAN view shows information about the local network connected IPv6 network.
| Option | Description | Comment |
|---|---|---|
| IP Address | IP address of the device on the local network. | Typically 192.168.1.1. |
WAN
The WAN view shows information about any connected IPv4 network.
| Option | Description | |
|---|---|---|
| IP Address | IP address for the device on the Internet. | |
| Gateway | IP address to the internet gateway. | |
| Primary DNS | First priority DNS server. | |
| Secondary DNS | Second priority DNS server. |
Clients
The Connected Clients view shows a list of clients connected to the network.
Table
| Column | Description | Comment |
|---|---|---|
| Hostname | Client hostname. | |
| MAC Address | Client MAC Address . | |
| IPv4 Address | Client IPv4 Address. | |
| IPv6 Address | Client IPv6 Address. | |
| Active Connections | Number of active connections. |
Routing
The Routing Status view shows the static routes configuration for the various network types.
IPv6 Neighbors
The IPv6 Neighbors view shows information about IPv6 devices in the network neighborhood.
ARP
The ARP status view shows information about ARP routes.
Table
The table displays information about static ARP routes.
| Column | Description | Comment |
|---|---|---|
| IPv4 Address | IPv4 Address. | |
| MAC Address | Client MAC Address . | |
| Device | Network device type. | Displayed as virtual interface name. |
IPv4
The IPv4 status view shows information about IPv4 routes.
Table
The table displays information about static IPv4 routes.
| Column | Description | Comment |
|---|---|---|
| IPv4 Address | IPv4 Address. | |
| Gateway | IP address to the internet gateway. | |
| Genmask | Route genmask. | |
| Device | Network device type. | Displayed as virtual interface name. |
IPv6
The IPv6 status view shows information about IPv6 routes.
Table
The table displays information about static IPv6 routes.
| Column | Description | Comment |
|---|---|---|
| IPv6 Address | IPv6 Address. | |
| Next Hop | Next Hop device. | |
| Device | Network device type. | Displayed as virtual interface name. |
IPv6 Neighbors
The IPv6 Neighbors view shows information about IPv6 devices in the network neighborhood.
Table
The table shows information about discovered IPv6 neighbors.
| Column | Description |
|---|---|
| Interface | Connected interface. |
| IP address | IPv6 address. |
| HW address | Hardware address. |
| Status | Device status. |
DHCP
The Active DHCP Leases view shows the status of any DHCP leases currently in use.
DHCPv4 Leases
| Column | Description |
|---|---|
| Hostname | Client hostname. |
| IPv4 Address | Client IPv4 Address. |
| MAC Address | Client MAC Address. |
| Leasetime remaining | Time until the lease expires. |
DHCPv6 Leases
| Column | Description |
|---|---|
| Hostname | Client hostname. |
| IPv6 Address | Client IPv6 Address. |
| DUID | Client DUID. |
| Leasetime remaining | Time until the lease expires. |
NAT
The NAT view shows a list of active NAT mappings in the device network.
Connections
The Active Connections gauge shows how many NAT mappings are in use out of the allowed total, as a percentage and as a count.
NAT Connection Table
Connections to and from the local network to the external network are added to the table, allowing the device to handle traffic routing decisions.
The table displays information about active NAT connections.
| Column | Description | Comment |
|---|---|---|
| Protocol | Communication protocol used. | |
| Source | Internal IP address. | |
| Destination. | External IP address. | |
| Source Port | Internal Port. | |
| Destination Port | External Port. |
WiFi
The WiFi Status view shows information about the wireless network, and allows you to scan the local area for other wireless access points.
WiFi
The general WiFI Status view displays information about your wireless channels and network interfaces.
WiFi Scan
The WiFi scan view allows you to scan the area around the device to find out what other access points are visible.
WiFi
The general WiFI Status view displays information about your wireless channels and network interfaces.
Configuration
For each wireless radioinformation is displayed about:
- WiFi channel in use.
- Noise level in dB for the channel.
- WiFi interface name.
- WiFi encryption used by the interface.
Client
For each connected client, more infomation about the connected client is available.
Details
To view more details about a client, click the expand button.
| Item | Description | Example |
|---|---|---|
| IP-Address | Client IPv4 address. | 10.0.0.154 |
| MAC-Address | Client MAC address. | 1A:97:1C:C7:76:63 |
| DHCP | Does client use DHCP? | true |
| Idle | Is the device transmitting? | 0 |
| In Network | ID for connected network. | 74 |
| RSSI | Received signal strength indicator value. | -42 dBm |
| SNR | Signal to Noise Ratio value. | 41 dB |
| Number of Antennas | Client antennas in use. | 2 |
| TX Rate | Transmission rate. | 130 Mbps |
| RX Rate | Receive rate. | 144 Mbps |
| Flags | Provided device flags. | BRCM, WME, N_CAP, AMPDU |
| HT Capabilities | Supported HT Capabilities (data rates). | LDPC, BW40, SGI20, SGI40 |
| TX Total Packets | Total number of transmitted packets. | 22589 |
| Unicast Packets | Total packets transmitted through unicast. | 224 |
| TX Unicast Packets | Packets transmitted through unicast. | 224 |
| TX Multicast/Broadcast Packets | Packets transmitted through multicast. | 22365 |
| TX Failures | Transmission failures. | 0 |
| RX Data Packets | Received packets. | 440 |
| RX Unicast Packets | Received packets transmitted through unicast. | 209 |
| RX Multicast/Broadcast Packets | Received packets transmitted through multicast. | 231 |
| TX Data Packets Retried | Resent data packets. | 0 |
| TX Total Packets Sent | Total data packets transmitted through unicast. | 7 |
| TX Packets Retries | Retransmitted data packets. | 1 |
| TX Packets Retry Exhausted | Data Packets failed after retry. | 0 |
| RX Total Packets Retried | Retransmitted data packets. | 107 |
<a data-curid=“true” href=“:ade:status:wifi:scan:start&fullpage&noreadmore}}
Band Steering
The Band Steering view shows information about band steering.
Status
The status section shows the current band steering status.
The information is displayed in the STA info summary table.
| Column | Description |
|---|---|
| STAMAC | Station (client) MAC address. | | Interface | Client interface name. | | TimeStamp | Timestamp for the steering event. | | Txrate | Transmission rate. |
| RSSI | Received signal strength indicator . |
| Bounce | Does the client bounce back to a particular bandafter steering? (yes/no). |
| Picky | Does the client prefer a particular band? (yes/no). |
| PSTA | Is the client a proxy station? (yes/no). |
| DUALBAND | Is the client dual-band capable? (yes/no). |
Log
The log section contains the log file, which shows the band steering events.
The information is displayed in the Band Steering Record table.
| Column | Description |
|---|---|
| Seq | |
| TimeStamp | Timestamp for the steering event. |
| STAMAC | Station (client) MAC address. | | Fmch | From channel (hex code). |
| To_ch | To channel (hex code). |
| Reason | Event (hex code). |
| Description | Description of event. |
DSL
The DSL status view shows information about any DSL connections to the device.
DSL Status Information
The DSL Status Information section shows the status for the DSL line.
Line Status
| Status | Description |
|---|---|
| Idle | No connection. |
| Handshake | Searching for connection, negotiating transfer. |
| Training | Connection found, testing cable. |
| Showtime/Active | Connection established. |
DSL Mode
The DSL Mode section shows the DSL.
Bit Rate
The Bit Rate section shows transmission rates for streams in bits per second (bps).
Actual Data Rate
| Column | Description |
|---|---|
| Downstream | Rate to the device. |
| Upstream | Reate from the device. |
Operating Data
The Operating Data section shows signal strength for the DSL line.
SNR margin
The SNR Margin section displays the signal-to-noise margin for the streams.
| Column | Description |
|---|---|
| Downstream | To the device. |
| Upstream | From the device. |
Loop Attentuation
The Loop Attentuation section shows signal attentuation for the streams.
| Column | Description |
|---|---|
| Downstream | To the device. |
| Upstream | From the device. |
Error Counter
The Error Counter section lists the number of (discovered) errors for the connection.
FEC Corrections
The FEC Corrections table shows FEC corrections for the streams.
| Column | Description |
|---|---|
| Downstream | To the device. |
| Upstream | From the device. |
CRC Corrections
The CRC Corrections table shows CRC corrections for the streams.
| Column | Description |
|---|---|
| Downstream | To the device. |
| Upstream | From the device. |
Cell Statistics
The Cell Statistics section shows the number of cells transmitted for the streams.
| Column | Description |
|---|---|
| Received | To the device. |
| Transmitted | From the device. |
IGPM TV
The IGPM TV Status views shows information about your IPTV services and their connection status.
Configuration
The table shows any connected IGMP TV channels and information about each:
USB
The USB devices views displays information about any USB devices connected to the gateway device.
Note: Supported file systems for USB devices are NTFS and FAT32.
Table
The USB device information table shows information about the USB devices.
| Column | Description | Comment |
|---|---|---|
| Device ID | Identification for the USB device. | |
| Vendor ID | Identification for the manufacturer. | |
| Vendor Name | Name of the manufacturer. | |
| Device Name | Name reported by the USB device. |
CATV
The CATV Status view shows information about CATV services connected to the device.
Note: Available on EG300 & EG400 only.
| Option | Description | Example |
|---|---|---|
| Inteno model | Model. | CATV-302 |
| VPD | Reverse voltage on Protection Device. | -inf dBm |
| RF | Range. | 75.7 dBµV |
| RF enable | Enable RF. | OFF |
SFP
The SFP Status view shows information about SFP connectors enabled in the device.
Configuration
Information is shown in two tables; ROM information and DDM information.
Note: Available on EG300 & EG400 only.
DDM
The DDM table shows information about the DDM retrieved from the SFP.
| Option | Description | Example |
|---|---|---|
| voltage | Port voltage. | 3.1872 (V) |
| current | Port current. | 26.448 (mA) |
| tx-pwr | Broadcasting power. | 0.3530 (mW) |
| tx-pwr-dBm | Broadcasting power. | -4.5223 (dBm) |
| rx-pwr | Received signal power. | 0.3026 (mW) |
| rx-pwr-dBm | Received signal power. | -5.1913 (dBm) |
| rx-pwr-type | Received power type. | average |
ROM
The ROM table shows information about the ROM.
| Option | Description | Example |
|---|---|---|
| connector | Connector type. | SC |
| ethernet | Ethernet type. | LX |
| encoding | Encoding type. | 8B10B |
| rate | Line rate. | 1300 |
| single-mode | Single mode distance. | 20000 |
| vendor | Port manufacturer or vendor. | Skylane Optics |
| oui | Organizationally Unique Identifier. | 00:25:cd |
| pn | Product name. | SBU35020DR3D000 |
| rev | ROM Revision. | A |
| sn | Serial Number | b19bmjrx1857 |
| date | ROM date. | 2016-04-21 |
| ddm | DDM version | 9.3 |
Diagnostics
The Diagnostic Utility allows you to perform diagnostic tests from the web interface.
Speed Test
The Speed Test view allows you to perform a TP Test for your network, using your device as the endpoint.
Ping
The Ping Test view allows you to perform a Ping for a selected host.
Ping Test
To perform a ping test against an endpoint:
- Enter a valid hostname or IP address in the Host to ping box
- Click Ping
The result of the ping is shown below the utility.
Example:
PING 127.0.0.1 (127.0.0.1): 56 data bytes 64 bytes from 127.0.0.1: seq=0 ttl=64 time=0.208 ms 64 bytes from 127.0.0.1: seq=1 ttl=64 time=0.130 ms 64 bytes from 127.0.0.1: seq=2 ttl=64 time=0.129 ms 64 bytes from 127.0.0.1: seq=3 ttl=64 time=0.146 ms 64 bytes from 127.0.0.1: seq=4 ttl=64 time=0.130 ms --- 127.0.0.1 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max = 0.129/0.148/0.208 ms
Trace
The Tracing tool view allows you to perform a Traceroute Test for a selected host.
Traceroute Test
To perform a ping test against an endpoint:
- Enter a valid hostname or IP address in the Host to trace box
- Click Trace
The result of the trace is shown below the utility.
Example:
Trace results:
traceroute to 127.0.0.1 (127.0.0.1), 30 hops max, 38 byte packets 1 127.0.0.1 0.033 ms
Speed Test
The Speed Test view allows you to perform a TP Test for your network, using your device as the endpoint.
Configuration
| Option | Description | Comment |
|---|---|---|
| Direction | Traffic direction to test. | Up and Down, Up, Down. |
| Package Size | Size of test data packages to send. | Size of test packages to send. |
| Speedtest Server | Server to use for the test. | A number of default servers are provided, but you can edit the list. |
Perform Speed Test
Example
Test results:
Downstream: 103.45 Mbit/s Upstream: 44.10 Mbit/s
Add test server
If you have additional test servers you want to use, you can add them to the dropdown list.
To add a test server:
- Click the + plus sign
A dialog is shown allowing you to enter parameters:
- Add a valid Server Hostname
- Add a valid server Port
- Click OK
Remove test server
Servers in the test server list can be removed.
To remove a test server:
- Select the server in the Speedtest Server list
- Click the - minus sign
The server is removed from the list immediately.
Realtime Graphs
The Realtime Graphs view provides access to graphical representations of status for the device. The graphs scroll as time progresses and lines indicate the current status.
Overview
Connections
The Connections graph shows the number of currently active connections for the device.
Graph Lines
Voice
The Voice Status view shows information about SIP accounts, phone numbers and voice lines connected to the device.
Configuration
Information is shown in two tables.
Your phone numbers
| Option | Description | Comment |
|---|---|---|
| Name | SIP account name. | Uses type and number unless otherwise set. |
| User | SIP user. | |
| Domain | SIP domain. | |
| Registration interval | SIP registration interval domain. | |
| Last registration | Last registration time. | |
| Status | Current status of the line. |
Voice lines
The Voice lines shows a list of connected voice lines.
| Option | Description | |
|---|---|---|
| Name | Voice line name. | Uses type and number unless otherwise set. |
| State | Current state of the line. |
Event Log
The Event Log view lets you view and manage the event log for the device.
Log
The Log section contains log settings and lets you download the logs.
| Item | Description |
|---|---|
| Download All Logs | Save the logs to the local computer. |
| Limit Log List | Limit the number of events. |
| Filter Log Messages By Source | Filter out events by freetext search in source. |
| Filter By Type | Filter out event types by Logging level. |
| Filter By | Filter out events in the log (firewall / network / system / iptv). |
Enable Online Help
For JUCI version 3.10.0+, online help is enabled by default.
However, if you upgrade from an earlier version, this option may not have been enabled. If so, you may need to connect to your device via SSH and run console commands to enable the setting.
CLI Enable Online Help
To enable online help:
Commands on Local Computer
- Open a console window on your local computer.
- Connect to the device:
ssh admin@192.168.1.1
Note: The address may be different from 192.168.1.1 for your device. Use the same address as for the usual login.
Note: You may need to enable SSH access to your device from the System > Management > SSH.
Note: For login, use the password defined in System > Passwords.
Commands on Device
The command line commands to run are the following:
To enable the help:
uci set juci.wiki.visible=1
To apply the setting:
uci commit juci
Glossary
ABR
The Available Bit Rate (ABR) service type is used primarily for traffic that is not time sensitive and don't need service level guarantees.
Access point
An access point is a device or interface that connects users to other users within the network. I can also serve as the point of interconnection between the WLAN and a fixed wire network.
The number of required access points depends on the number of network users and the area the network covers.
Access Control List
An Access Control List (ACL) is an table containing permissions for a particular service or device, defining access to objects and allowed operations.
ACS
An Auto Configuration Servers (ACS) is a server used for automatic device and user provisioning and configuration through TR069.
ADPCM
Adaptive Differential Pulse-Code Modulation (ADPCM) is a differential pulse-code modulation variant where the size of quantization ranges is modified with a scaling factor before encoding. This means that the bandwidth requiremetns are reduced.
Ad SPECification
An ADvertisement SPECification (ADSPEC) is a part of an RSVP PATH message which contains information from network devices between a sender and receiver.
Typically the message allows advertise supprted services, availability and transmission information.
Assured Forwarding
Assured Forwarding (AF) is a mechanism for assurance of delivery, given a defined rate.
In case of congestion, traffic that exceeds the rate have a higher probability of being dropped.
The four AF classes have the same priority. For each class, packets are given a drop probability.
| Drop probability | Class 1 | Class 2 | Class 3 | Class 4 |
|---|---|---|---|---|
| Low | AF11 | AF21 | AF31 | AF41 |
| Medium | AF12 | AF22 | AF32 | AF42 |
| High | AF13 | AF23 | AF33 | AF43 |
AFTR
An Address Family Transition Router (AFTR) is a server implementing the Dual-Stack Lite to provide IPv4 to IPv4 communication over IPv6.
AMPDU
An Aggregated MAC Protocol Data Unit - AMPDU - is an aggregation of MPDUs.
AMSDU
An Aggregated MAC Service Data Unit is an aggregation of MSDUs.
APN
An Access Point Name (APN) is the name of a gateway between a mobile network providing access to Internet.
ARP
Address Resolution Protocol (ARP) is a protocol for mapping an Internet Protocol address (IP address) to a physical machine address that is recognized in the local network.
Airtime Fairness
ATF feature addresses the issue where low-speed data transfers impact high-speed data transfers.
Airtime Fairness gives equal amounts of air time (instead of equal number of frames) to each client regardless of its theoretical data rate. This will ensure higher download speed to latest devices when slower devices are connected to the same AP. This is done to prevent slower devices from penalizing faster devices by monopolizing network traffic.
In effect this means that Airtime Fairness improves the speed for faster devices by making the slowest devices even slower. This may allow better Quality of Service for faster devices, and should be negligible for the slower devices in most cases.
Using band steering in combination of Airtime Fairness can further improve results.
ATM - Asyncronous Data Transfer Mode
ATM - Asyncronous Data Transfer Mode is a protocol for high-throughput data traffic and streaming.
Auto-Negotiation
Auto-negotiation is a method in Ethernet where two devices agree on the best performance transmission mode they both support.
Back-Off
Back-Off is a method for decreasing the frequency of retransmissions of request in order to avoid congestion and collision.
Band Steering
Band steering allows the device to determin if a connected client is dual-band capable. If so, the client can be forced to use the less congested 5GHz network.
This is done by blocking the client from connecting to the 2.4GHz network.
Beamforming
Beamforming is technique used for radio signals to improve quality and performance. It is done by creating multiple signals and finding the best paths, thereby “shaping” the antenna output to provide minimum interference.
Bit Error Rate
The Bit Error Rate (BER) is the percentage of transmitted bits which contain errors.
Bitswap
Bitswap is a methoid for adjusting the number of bits allocated to channels. Congested channels are assigned fewer bits, and available channels are allocated more bits.
Bit Rate
The bit rate is a measure of traffic speed in a network. It indicates the number of bits per second transmitted.
BSS
The basic service set (BSS) is the basic building block in a wireless LAN. It is a set of all stations that can communicate with each other. Every BSS has an identification (ID) called the BSSID, which is the MAC address of the access point servicing the BSS.
CA
A Certificate Authority (CA) is an entity that issues digital certificates which guarantee that a public key is owned by the certificate subject, verifying their identity.
Certificates typically include the owner's public key, the expiration date of the certificate, the owner's name and other information about the public key owner.
CATV
Community Antenna TeleVision (CATV), or “cable TV”, is a system of delivering television programming radio frequency (RF) signals transmitted through coaxial cables or fiber-optic cables.
CBR
The Constant Bit Rate (CBR) service type is used for applications that transport traffic at a constant bit rate, where time synchronisation between source and destination is important, providing predictable response times and a static amount of bandwidth.
CCMP
CCMP – CTR mode with CBC-MAC Protocol is based on the Advanced Encryption Standard (AES) cipher along with strong message authenticity and integrity checking.
CDMA
Code division multiple access (CDMA) is a radio communication standard, where several transmitters can send information simultaneously over a single channel.
Cell (DSL)
DSL cells are ATM data encoded into small, fixed-sized packets (frames).
CHAP
Challenge Handshake Authentication Protocol (CHAP) is a method used to authenticate PPP sessions.
CHAP uses a randomly generated string as a unique challege phrase for each authentication. This is combined with device host names and hash functions so that no static secret information is sent.
Checksum
A checksum is a value used as an error control mechanism. It works by calculating a sum for the data using a predefined algorithm, and then comparing the result to some expected value, or the checksum itself. If the result is not as expected, this indicates that something has gone wrong in transmission.
Cipher
A WiFi security cipher is the method through which a connection is secured against intrusion.
For information about cipher strings, see https://www.openssl.org/docs/manmaster/apps/ciphers.html.
Circuit ID
A Circuit ID is a unique identifier assigned to a network connection between two locations.
Classful QDisc / Packet Scheduler
A Classful QDisc is a Quality Of Service function containing classes. The classes may contain other QDiscs, which un turn can be classful or classless.
CLR
Cell Loss Ratio (CLR) is the percentage of network cells that do not arrive at their destination.
Codec
A coder-decoder (codec) is a method for encoding or decoding digital data streams or signals. It uses various algorithms to encode data for transmission or storage, or decodes encoded data for use.
Companding
A compressing-expanding (companding) is a method for managing dynamic range in channels with limited dynamic range. It compresses the dynamic range of a signal transmission and expands it at the receiving end, according to the defined.
Congestion
Network congestion is when the traffic volume in the network becomes so large it affects the trasnmission and delivery of data packets, thereby causing a reduced quality of service.
Connection Bytes
Connection Bytes is a filtering property that matches packets only after the specified number of bytes has been transfered through the connection.
CPE
The term Customer-Premises Equipment (CPE) is used in TR069 and refers to devices in a network that is located in the premises of a subscriber.
%CPU
The CPU percentage for a process indicates how much of CPU processing power is being used.
CPU
The CPU value indicates how much of CPU processing power is being used.
CRC
Cyclic Redundancy Check (CRC) is a method for discovering errors in data transmission by verifying the received data against an attached check value.
Cron Log Level
The Cron Log level determines how much information to display or write to file when creating system logs.
| Level |
|---|
| Everything |
| High Verbosity |
| Low Verbosity |
| Executions and Errors |
| Only Errors |
Class Selector
The Class Selector (CS) is used by Differentiated Services as a precedence code point value that maps to a Differentiated Services Code Point. It is backwards compatible with IP precedence values.
Data Package
A data package is a portion of data that transmitted between a source and destination in a network, normally of larger size.
Dynamic DNS (DDNS or DynDNS)
Dynamic DNS (DDNS) is a method for automatically providing DNS servers with up to date information about configured hostnames and addresses.
DECT
DECT - Digital Enhanced Cordless Telecommunications is a European standard for cordless telephone systems over radio.
In the United States a slightly different radio frequency range is used, and it is called DECT 6.0.
Delay
Network delay is a network characteristic indicating how long it takes for a piece of data to travel across the network.
Device Flags
The Device Flags field shows information about the physical device.
DFS
Dynamic Frequency Selection (DFS) means that the wireless radio automatically selects the least congested wifi channel to use.
DHCP lease
A DHCP Lease is a DHCP is a reservation of a particular IP address provided to a client by a DHCP server. It is called lease because it expires aftrer a certain amoutn of time (usually 24 hours. Before the lease expires, the DHCP server should renew the lease or provide a new lease.
DHCP Options
When sending DHCP requests, additional options can be requested by providing a space separated list of codes.
| Code | Description |
|---|---|
| 0 | Pad. |
| 1 | Subnet Mask. |
| 2 | Time Offset(deprecated). |
| 3 | Router. |
| 4 | Time Server. |
| 5 | Name Server. |
| 6 | Domain Name Server. |
| 7 | Log Server. |
| 8 | Quote Server. |
| 9 | LPR Server. |
| 10 | Impress Server. |
| 11 | Resource Location Server. |
| 12 | Host Name. |
| 13 | Boot File Size. |
| 14 | Merit Dump File. |
| 15 | Domain Name. |
| 16 | Swap Server. |
| 17 | Root Path. |
| 18 | Extensions Path. |
| 19 | IP Forwarding enable/disable. |
| 20 | Non-local Source Routing enable/disable. |
| 21 | Policy Filter. |
| 22 | Maximum Datagram Reassembly Size. |
| 23 | Default IP Time-to-live. |
| 24 | Path MTU Aging Timeout. |
| 25 | Path MTU Plateau Table. |
| 26 | Interface MTU. |
| 27 | All Subnets are Local. |
| 28 | Broadcast Address. |
| 29 | Perform Mask Discovery. |
| 30 | Mask supplier. |
| 31 | Perform router discovery. |
| 32 | Router solicitation address. |
| 33 | Static routing table. |
| 34 | Trailer encapsulation. |
| 35 | ARP cache timeout. |
| 36 | Ethernet encapsulation. |
| 37 | Default TCP TTL. |
| 38 | TCP keepalive interval. |
| 39 | TCP keepalive garbage. |
| 40 | Network Information Service Domain. |
| 41 | Network Information Servers. |
| 42 | NTP servers. |
| 43 | Vendor specific information. |
| 44 | NetBIOS over TCP/IP name server. |
| 45 | NetBIOS over TCP/IP Datagram Distribution Server. |
| 46 | NetBIOS over TCP/IP Node Type. |
| 47 | NetBIOS over TCP/IP Scope. |
| 48 | X Window System Font Server. |
| 49 | X Window System Display Manager. |
| 50 | Requested IP Address. |
| 51 | IP address lease time. |
| 52 | Option overload. |
| 53 | DHCP message type. |
| 54 | Server identifier. |
| 55 | Parameter request list. |
| 56 | Message. |
| 57 | Maximum DHCP message size. |
| 58 | Renew time value. |
| 59 | Rebinding time value. |
| 60 | Class-identifier. |
| 61 | Client-identifier. |
| 62 | NetWare/IP Domain Name. |
| 63 | NetWare/IP information. |
| 64 | Network Information Service+ Domain. |
| 65 | Network Information Service+ Servers. |
| 66 | TFTP server name. |
| 67 | Bootfile name. |
| 68 | Mobile IP Home Agent. |
| 69 | Simple Mail Transport Protocol Server. |
| 70 | Post Office Protocol Server. |
| 71 | Network News Transport Protocol Server. |
| 72 | Default World Wide Web Server. |
| 73 | Default Finger Server. |
| 74 | Default Internet Relay Chat Server. |
| 75 | StreetTalk Server. |
| 76 | StreetTalk Directory Assistance Server. |
| 77 | User Class Information. |
| 78 | SLP Directory Agent. |
| 79 | SLP Service Scope. |
| 80 | Rapid Commit. |
| 81 | FQDN, Fully Qualified Domain Name. |
| 82 | Relay Agent Information. |
| 83 | Internet Storage Name Service. |
| 84 | N/A |
| 85 | NDS servers. |
| 86 | NDS tree name. |
| 87 | NDS context. |
| 88 | BCMCS Controller Domain Name list. |
| 89 | BCMCS Controller IPv4 address list. |
| 90 | Authentication. |
| 91 | Client-last-transaction-time. |
| 92 | Associated-ip. |
| 93 | Client System Architecture Type. |
| 94 | Client Network Interface Identifier. |
| 95 | LDAP, Lightweight Directory Access Protocol. |
| 96 | N/A |
| 97 | Client Machine Identifier. |
| 98 | Open Group's User Authentication. |
| 99 | GEOCONF_CIVIC. |
| 100 | IEEE 1003.1 TZ String. |
| 101 | Reference to the TZ Database. |
| 102-111 | N/A |
| 112 | NetInfo Parent Server Address. |
| 113 | NetInfo Parent Server Tag. |
| 114 | URL. |
| 115 | N/A |
| 116 | Auto-Configure |
| 117 | Name Service Search. |
| 118 | Subnet Selection. |
| 119 | DNS domain search list. |
| 120 | SIP Servers DHCP Option. |
| 121 | Classless Static Route Option. |
| 122 | CCC, CableLabs Client Configuration. |
| 123 | GeoConf. |
| 124 | Vendor-Identifying Vendor Class. |
| 125 | Vendor-Identifying Vendor-Specific. |
| 126 - 127 | N/A |
| 128 | TFPT Server IP address. |
| 129 | Call Server IP address. |
| 130 | Discrimination string. |
| 131 | Remote statistics server IP address. |
| 132 | 802.1P VLAN ID. |
| 133 | 802.1Q L2 Priority. |
| 134 | Diffserv Code Point. |
| 135 | HTTP Proxy for phone-specific applications. |
| 136 | PANAAuthentication Agent. |
| 137 | LoSTServer. |
| 138 | CAPWAP Access Controller addresses. |
| 139 | OPTION-IPv4_Address-MoS. |
| 140 | OPTION-IPv4_FQDN-MoS. |
| 141 | SIP UA Configuration Service Domains. |
| 142 | OPTION-IPv4_Address-ANDSF. |
| 143 | OPTION-IPv6_Address-ANDSF. |
| 144 - 149 | N/A |
| 150 | TFTP server address. |
| 150 | Ether boot. GRUB configuration path name. |
| 151-174 | N/A |
| 175 | Ether boot. |
| 176 | IP Telephone. |
| 177 | Ether boot. Packet Cable and Cable Home. |
| 178- 207 | N/A |
| 208 | pxelinux.magic (string) = F1:00:74:7E (241.0.116.126). |
| 209 | pxelinux.configfile (text). |
| 210 | pxelinux.pathprefix (text). |
| 211 | pxelinux.reboottime (unsigned integer 32 bits). |
| 212 | OPTION_6RD. |
| 213 | OPTION_V4_ACCESS_DOMAIN. |
| 214-219 | N/A |
| 220 | Subnet Allocation. |
| 221 | Virtual Subnet Selection. |
| 222-223 | N/A |
| 224-254 | Private use. |
| 255 | End. |
DHCP Pool
A DHCP pool is a collection of IP addresses available for DHCP allocation.
The Pool Start number is the first available number in the pool.
The Pool Size is the count of available numbers, counting from the pool start.
Example: with Pool Start of 50 and a Pool Size of 100, the available pool addresses are 50 to 150.
DNS Server
A DHCP server is a server that provides IP addresses to clients on the a network.
See also: Domain Name System.
Dial Plan
A dial plan defines what sequence of digits need to be dialled in the private branch exchange to get access to specific calling networks or enable other features.
Differentiated Services
Differentiated Services (DiffServ) is a method for classifying traffic and providing quality of service for IP networks.
DiffServ uses a differentiated services code point in the IP header for packet classification purposes.
DLNA
Digital Living Network Alliance (DLNA) is designed to act as a bridge between media and device. It needs either a wired or a wireless network.
Discrete MultiTone Modulation
Discrete MultiTone Modulation is a modulation method where the available bandwidth is divided into a large number of channels. Data is allocated to maximize the throughput of every channel. Channels that can't carry data are not used, and the bandwidth reallocated.
DMT is the technology which divides the whole bandwidth on the telephone line into lots of sub-channels and then controlling these 'virtual modems' as one together in order to get higher speeds.
DMZ
DMZ (demilitarized zone) is used to provide an extra layer of security. It's a network added between a protected network and an external network.
DNS
The Domain Name System (DNS) is a hierarchical decentralized naming system for computers, services, or any resource connected to the Internet or a private network.
DNS Server
A Domain Name System Server runs networking software containing a database of network names and addresses to resources on the internet.
Domain Name
A domain name is typically a name that identifies a resource on the internet with an IP address, according to the Domain Name System.
Downlink
A Downlink interface is an interface to subscribers/clients.
DCPM
Differential Pulse-Code Modulation (DPCM) is a signal encoding method that uses pulse code modulation as a baseline and then compares nearby values to encode a difference instead of a fixed value.
Dropping
Dropping is when a packet is deliberately dropped due to congestion or other reasons, such as quality of service rules.
DSCP
A Differentiated Services Code Point (DSCP) is a 6-bit code point in the differentiated services field (DS field) inside the packet IP header.
It is used by Differentiated Services for classification purposes to provide quality of service functionality.
DSL
DSL – Digital Subscriber Line is a way of providing high bandwidth data communication through regular copper telephone lines.
DS-Lite
Dual-Stack Lite (DS-Lite) is amethod for sharing of IPv4 addresses by combining IPv4-in-IPv6 and NAT.
DTMF
Dual Tone - Multi Frequency (DTMF) is a signalling method for telephone systems, which uses a set of eight audio frequencies transmitted in pairs to represent 16 signals, represented by the ten digits, the letters A to D, and the symbols # and *.
DTMF Mode
The DTMF mode is a setting that governs how Dual Tone Multi Frequency signalling is to be performed.
DUID
The DHCP Unique IDentifier – DUID – is a unique identifier associated with each client and server in a DHCP environment. The DUID should be permanently stored and not changed.
Duplex
The term duplex indicates how traffic is performed. It can be either:
- Half - only one side can communicate at a time.
- Full - both sides can communicate with each other simultaneously.
Dwell Time
The dwell time is the amount of time spent on each channel in the hopping sequence when hopping from channel to channel.
Ethernet Auto Power Down
Ethernet Auto Power Down allows the hardware ports to be turned off automatically when not in use.
EDNS
Extension mechanisms for DNS - EDNS - is a specification for expanding the size of several parameters of the Domain Name System DNS protocol.
EDNS adds information to DNS messages in the form of pseudo-resource-records included in the “additional data” section of a DNS message in both requests and responses.
EDNS is needed for DNS Security Extensions.
EEE
Energy-Efficient Ethernet (EEE) is a technology for allowing for less power consumption during periods of low data activity.
ESP
Encapsulating Security Payload (ESP) is a security protocol for network data in IPv4 and IPv6 networks.
Ethernet
Ethernet a family of computer networking technologies commonly used in LANs.
Communication over ethernet consists of data frames. Each frame contains source and destination addresses, and error-checking data.
EVDO
Evolution-Data Optimized (EVDO) is a standard for broadband Internet through wireless data transmission.
Failover
Failover means switching over to a different network when the selected network cannot be accessed.
FEC - Forward error correction
Forward error correction entails encoding the signal with redundant information that can be matched to discover errors in the transmission.
Firewall Action
The firewall action defines how traffic is handled by the firewall.
| Item | Description |
|---|---|
| ACCEPT | Allow the traffic. |
| REJECT | Refuse the traffic. |
| DROP | Ignore the traffic. |
| FORWARD | Pass the traffic along. |
Firewall group
A firewall group is a collection of IP addresses that have the same firewall rules.
Flow Specification
A flow specification defines data traffic contents and requirements, and is used by devices to decide how to handle packets on the network. It consists of two parts - a Traffic SPECification, which describe traffic parameters an a Request SPECification that defines requirements for the flow.
Frame
In networking, a frame is a unit of data, consisting of addressing and synchronization information around a payload with data to be transmitted.
Frames of smaller size are often encapsulated in larger frames.
Gateway
A gateway is a node in a network that provides interconnectivity between networks of different types.
For a basic Internet connection, the gateway provides Internet access to the local network.
Gateway metric
The gateway metric is used for routing decisions, and is added to routing tables to enable routing decisions.
Genmask
A genmask is the netmask for the destination net. For example 255.255.255.255 for a host destination and 0.0.0.0 for the default route.
GRE
Generic Routing Encapsulation (GRE) is a multipurpose tunneling protocol using IP networks to encapsulate a number of different network layer protocols.
GSM
Global System for Mobile Communications (GSM) is a standard for protocols for digital cellular networks used by mobile phones.
Host ID
A host ID is a ( IPv6 label assigned to a network device used to identify the device in the network for addressing purposes.
Hostname
A hostname is a (IPv4 label assigned to a network device used to identify the device in the network for addressing purposes.
HSPA / HSPA+
High Speed Packet Access (HSPA) is an extension of 3G mobile networks utilizing WCDMA.
Evolved High Speed Packet Access (HSPA+) is a furhter improvement on HSPA allowing for higher speeds.
HT Capabilities
HT Capabilities are information about which data rates are supported by a device or network.
ICMP
The Internet Control Message Protocol (ICMP) is used to send error messages about services or device status.
IGMP
IGMP – Internet Group Management Protocol is a communications protocol used on IPv4 networks to establish multicast group memberships.
IGMP Proxy
An Internet Group Management Protocol (IGMP) Proxy is a setting to enable the device to handle IGMP host tasks such as sending membership and leave group membership reports to groups.
IGMP Snooping
IGMP snooping is the process of listening to IGMP network traffic to determine which paths are associatied with which IP multicast streams, and allow management of the multicast traffic.
Inotify
Inotify (inode notify) is a subsystem to detect changes to the filesystem, and report those changes to applications.
Interface Protocol
The Interface Protocol setting defines the protocol/behavior for an interface.
| Protocol | Description |
|---|---|
| Unmanaged | No defined protocol. |
| Static Address | Static IP address. |
| DHCP v4 | Retrieve IPv4 address through DHCP |
| DHCP v6 | Retrieve IPv6 address through DHCP |
| PPP | PPP interface. |
| PPP over Ethernet | PPPoE interface. |
| PPP over ATM | PPPOA interface. |
| 3G | PPP over GPRS/EVDO/CDMA/UMTS |
| 4G | 4G interface over LTE / HSPA+. |
| Point-to-Point Tunnel | PTPT interface. |
| IPv6 Tunnel in IPv4 | 6in4 interface. |
| IPv6 Tunnel in IPv6 | 6to4 interface. |
| IPv6 rapid deployment | 6rd interface. |
| Dual Stack Lite | DS-lite interface. |
| PPP over L2TP | PPP over L2TP. |
Interface Protocol Type
The Interface Protocol Type defines the interface basic type and direction.
Uplink
An uplink interface type is an interface to services.
Downlink
A Downlink interface is an interface to subscribers/clients.
Unmanaged
The interface protocol type Unmanaged means that the connection has no defined protocol.
Interface Type
The Interface Type defines the base settings for the interface.
| Type | Description |
|---|---|
| Standalone | Not requiring hardware. |
| Any WAN | Any WAN interface. |
| Bridge | Network bridge. |
IntServ
Differentiated Services (DiffServ) is a method for classifying traffic and providing quality of service for IP networks.
DiffServ uses RSVP to handle traffic flow management.
Iopsys
Iopsys stands for Inteno Open Platform System. It combines the efficiency and power of the SOC (System on Chip) with the OpenWrt open source distribution. It further enables the operator to leverage on the modularity of OpenWrt to integrate new applications to the CPE.
IP Address
An Internet Protocol address (IP address) is a numerical identifier for a device address.
IPv4
Internet Protocol Version 4 - IPv4 - is the first major version of the Internet Protocol.
IP Route
Iproute2 is a collection of Linux utilities for handling routing, network interfaces, tunnels, traffic control, network-related device drivers, and other aspects.
IPtables
Iptables is a firewall application that uses configured tables to determine firewall rules and routes.
IPTV
Internet Protocol Television (IPTV) delivers television services over IP networks as a streaming service.
IPUI
International Portable User Identity (IPUI), is a unique identifier for each DECT Handset, allowing it to be assigned a SIP identity. The identifier is a 10-digit (40-bit) hexadecimal code
IPv4
An IPv4 address is an IP address represented as four groups separated by a period. Each group consists of decimal numbers between 0 and 255.
An example of an IPv4 address is 192.168.22.12.
IPv4
An IPv4 address is an IP address represented as four groups separated by a period. Each group consists of decimal numbers between 0 and 255.
An example of an IPv4 address is 192.168.22.12.
IPv4 Broadcast Address
Broadcast addresses in IPv4 networks are special values in the host-identification part of an IP address.
IPv6 Address
An IPv6 address is an IP address address represented as eight groups separated by colons (:). Each group contains four hexadecimal digits.
An example of an IPv6 address is 2011:09bd:583a:0000:8a2e:0000:0370:7334.
IPv6 Address
An IPv6 address is an IP address address represented as eight groups separated by colons (:). Each group contains four hexadecimal digits.
An example of an IPv6 address is 2011:09bd:583a:0000:8a2e:0000:0370:7334.
IP Address
An Internet Protocol address (IP address) is a numerical identifier for a device address.
IPv4
Internet Protocol Version 4 - IPv4 - is the first major version of the Internet Protocol.
IP Datagram
A IP datagram is a unit of data transmitted using the IP protocol, following a specific format which describes various aspects of the datagram, its source and its destination.
The IPv4 datagram consists of the following headers and fields:
| Bits | Name | Description |
|---|---|---|
| 4 | VERS | IP version number 0100 (4) or 0110 (6). |
| 4 | HLEN | Header length in 32-bit words, so if the number is 6, then 6 x 32 bit words are in the header i.e. 24 bytes. The maximum size is 15 x 32-bit words which is 60 bytes. The minimum size is 20 bytes or 5 x 32-bit words. |
| 8 | Type of Service | The TOS field. |
| 16 | Total Length | is the number of octets that the IP datagram takes up including the header. The maximum size that an IP datagram can be is 65,535 octets. |
| 16 | Identification | The Identification is a unique number assigned to a datagram fragment to help in the reassembly of fragmented datagrams. |
| 3 | Flags | Bit 0 is always 0 and is reserved. Bit 1 indicates whether a datagram can be fragmented (0) or not (1). Bit 2 indicates to the receiving unit whether the fragment is the last one in the datagram (1) or if there are still more fragments to come (0). |
| 13 | Frag Offset | in units of 8 octets (64 bits) this specifies a value for each data fragment in the reassembly process. Different sized Maximum Transmission Units (MTUs) can be used throughout the Internet. |
| 8 | TTL | the time that the datagram is allowed to exist on the network. A router that processes the packet decrements this by one. Once the value reaches 0, the packet is discarded. |
| 8 | Protocol | Layer 4 protocol sending the datagram, UDP uses the number 17, TCP uses 6, ICMP uses 1, IGRP uses 88 and OSPF uses 89. |
| 16 | Header Checksum | Header checksum error control. |
| ?? | IP Options | Optional field for testing, debugging and security. |
| ?? | Data | Packet contents, actual data. |
| ?? | Padding | Optionally, padding is added to make the datagram into multiples of 32 bits. |
IP ECN
The IP Explicit Congestion Notification (ECN) field is part of the IP TOS IP header field.
It is used to signal that the network is, or is about to, experience congestion.
A device can use the ECN field to mark a packet instead of dropping it. The receiver of the packet repeats the ECN back to the sender, which can reduce the transmission rate.
ECN uses the two last bits of the TOS field encode four different codepoints:
| Binary | Value | Description |
|---|---|---|
| 00 | Non-ECT | Non ECN-Capable Transport. |
| 10 | ECT(0) | ECN Capable Transport. |
| 01 | ECT(1) | ECN Capable Transport. |
| 11 | CE | Congestion Encountered. |
IP in IP
IP in IP is an method to provide data tunneling by encapsulating one IP packet in another IP packet, using header information.
IP Precedence
IP precedence is a method to assign priority to data packets by using part of the Type of Service field in the IP datagram header.
With IP precedence, the first three bits of the TOS field is used to provide one of eight possible precedence values.
| Binary | Value | Priority |
|---|---|---|
| 000 | (0) | Routine |
| 001 | (1) | Priority |
| 010 | (2) | Immediate |
| 011 | (3) | Flash |
| 100 | (4) | Flash Override |
| 101 | (5) | Critical |
| 110 | (6) | Internetwork Control |
| 111 | (7) | Network Control |
IP Quality of Service Algorithm
The IP Quality of Service Algorithm determines which type of QoS to provide; Strict Priority Precedence or Weighted Fair Queuing.
Strict Priority Precedence
Strict Priority Precedence means that where the the packets with the highest priority always are sent first.
Weighted Fair Queuing
Weighted Fair Queuing means that bandwidth is adjusted automatically according to traffic priority and weight value.
IP TOS
The IP Type of Service (TOS) field (also known as DiffServ or DSCP field) is a part of an IP datagram header, originally meant to describe the purpose of a datagram.
It is used by Differentiated Services for the DiffServ Code Point, and the optional Explicit Congestion Notification.
IUP
Inteno Universal Provisioning (IUP) is a technology for automatic delivery of service configuration and device settings.
Jitter
Jitter is variations in packet arrival time, which may be caused by network congestion, timing delays, or changed routes.
Jitter Buffer
A jitter buffer is storage for voice packets so they can be sent out in evenly spaced intervals used to reduce jitter, providing better transmission reliability.
There are two jitter buffer implementation types which are used by the SIP channel reciever.
| Implementation | Description |
|---|---|
| Fixed | Use a fixed buffer size. |
| Adaptive | Use a variable buffer size. |
JUCI
JUCI (Java User Control Interface) provides a command line and graphical user interface for administration of devices.
L2TP
Layer 2 Tunneling Protocol (L2TP) is a protocol used to support VPNs, where security is provided in the transmitted packages rather than in the tunneling.
LAN
LAN – Local Area Network is a number of connected units within a limited area, typically a building.
Latency
Latency is the time it takes for a packet of data to get from source to destination, normally measured by performing a round-trip test: sending a packet that is returned to the sender.
Latency Path
The DSL Latency Path comes in three modes: Path 1 (Fast), Path 2 (Interleaved) and Both 1 & 2. Fast is used for applications sensitive to delay. Interleaved suits applications sensitive to errors.
LCP
The Link Control Protocol (LCP) is part of the Point-to-Point Protocol and is used to set up the PPP connection.
Lease Time
Client lease time or lease time is the length of time a local device retains an IP address.
Link Speed
The link speed for a connection is the maximum transmission rate the device can provide. The actual speed may be lower.
LLC
The logical link control (LLC) layer provides multiplexing to enable different network protocols to coexist and be transported over the same network medium.
Load Balancing
Load balancing distributes traffic over multiple networks to provide an even load on each WAN interface.
Logging Level
The Logging level determines how much information to display or write to file when creating system logs.
Error messages come with a identifying level tag which makes it possible to filter out messages according to severity.
| Level |
|---|
| Emergency |
| Alert |
| Critical |
| Error |
| Warning |
| Notice |
| Info |
| Debug |
Loop Attenuation
Loop Attenuation is a measure of the quality of the line - how much the signal weakens over the loop.
Attenuation is measured in Decibel (dB). A value betwen 20dB-45dB can be considered normal.
LSAP
Link Service Access Point (LSAP) fields are used to identify which protocol handler should process an incoming frame.
LSAP fields allow the receiving node to pass each received frame to an appropriate device driver which understands given protocol.
MAC
A Media Access Control (MAC) address is a unique identifier for physical network interfaces.
Masquerading
Firewall masquerading entails modifying addressing to allow devices to communicate with the WAN without being visible externally. To the external network, all traffic will look as originating from the gateway.
MBS
Maximum Burst Size (MBS) is the maximum size of cells that can be transmitted in direct sequence on a particular connection.
MCR
The Minimum Cell Rate (MCR) defines the lowest rate at which cells can be transported in an ATM connection.
MIB
A management information base (MIB) is used in SNMP to describe the management data structure, in the form of a hierarchical namespace containing object identifiers (OID). Each OID identifies a variable that can be read or set via SNMP.
MPDU
A MAC Protocol Data Unit - MPDU - is a message transmitted to and from Media Access Control devices.
MSDU
A MAC Service Data Unit - MSDU - is a unit of data transmitted to and from Media Access Control devices, containing the packet and additional link layer information.
MSS
Maximum Segment Size (MSS) is a TCP parameter specifying the largest byte size a a single TCP segment can contain for a device.
MSS Clamping
Maximum Segment Size Clamping entails changing the maximum segment size of all TCP connections with a MTU lower than 1500.
MTU
Maximum Transmission Unit (MTU) is the largest physical packet size that a network can transmit. Any packets larger than the MTU are divided into smaller packets before being sent. MTU is measured in bytes.
Multicast
Multicast is group communication where information is addressed to a group of destination computers simultaneously.
IP multicast is a method of sending Internet Protocol data messages to a group of interested receivers in a single transmission. It is often employed for streaming media applications on the Internet and private networks. The method is the IP-specific version of the general concept of multicast networking.
It uses specially reserved multicast address blocks in IPv4 and IPv6.
In IPv6, IP multicast addressing replaces broadcast addressing as implemented in IPv4.
NAT
Network Address Translation (NAT) is a method to to device translate local network addresses into external addresses for the Internet.
NAT Loopback
NAT loopback is a method using NAT to provide access to services via the public IP address from inside the local network.
NAT-PMP
The NAT Port Mapping Protocol (NAT-PMP) is a network protocol to automatically detect and determine the NAT gateways to configure NAT settings and port forwarding.
NDP
The Neighbor Discovery Protocol - NDP - is an IPv6 protocol used for discovery and redirect similar to ARP and (ICMP](/glossary/i/icmp) for IPv4.
It us used to handle address configuration, node discovery, address determination, duplicate addresses detection, location of available routers and DNS servers, address prefix discovery, and maintainance of reachability information.
NDP defines five ICMPv6 packet types for communication:
Neighbor Advertisement
Neighbor advertisements are NDP discovery messages announcing the IP addresses of the node, and are sent in response to a Neighbor Solicitation message.
In NDP, Neighbor Advertisement packets have the type 136.
Netmask
A netmask is a mask used to divide an IP address into subnets and specify the network's available hosts.
For example, in 255.255.225.0, “0” is the assigned network address. In 255.255.255.255, “255” is the assigned broadcast address. The 0 and 255 are always assigned.
Network bridge
A network bridge combines two network segments inte an aggregated network, making them behave as if they are one continuos segment.
Network interface
A network interface is the access point between a device and a computer network. A network interface can be either a physical connection or a software access address.
Network Profile
A network profile is a global setting for your device that defines how it will work in the network.
For example, selecting a particular profile may configure your device as a wireless repeater or as a fully routed NAT gateway.
Depending on the selected profile, available features and settings will be different.
Some sample profiles:
Next Hop
Next hop refers to the next closest device a packet can go through, according to the routing table.
NIC
A Network Interface Controller – NIC, is an hardware component that connects a device to a network.
Noise level
The WiFi Noise level is the amount of interference in your wireless signal, such as crosstalk, radio frequency interference, distortion, and so on.
It is measured in decibels from zero to -120, where a lower value is better.
Typical environments range between -100db and -80db.
NTP - Network Time Protocol
NTP is a networking protocol for clock synchronization between devices in networks.
NTP Mode
The NTP Server mode allows the device to act as a local NTP server even when losing connection to the providing NTP server.
OBSS Coexistence
Overlapping basic service sets (OBSS) is a setting that configures the BSS to allow coexistence between 20 MHZ and 40 MHZ overlapping basic service sets (OBSS).
OpenWRT
OpenWrt is an open source distribution with an excellent overall user space environment, modular and flexible system design. It has a large and active development community.
More information:
More information and documentation is available at http://wiki.openwrt.org/.
OUI
An Organizationally Unique Identifier - OUI - is a 24-bit number used to uniquely identify a vendor.
Usually makes up the first three octets of the MAC address.
Overhead
Overhead is extra data or processing needed to manage delivery of a network data.
OSWD
The Open Web-Server Daemon - OSWD - handles web requests to the configuration framework. I allows access to device configuration services through the configuration framework.
Packet
A packet is a portion of data that transmitted between a source and destination in a network. It normally a smaller part of some larger unit of data, which is tagged with an identification number and an address. When all packets for a specific data unit arrives at their destination, they are reassembled to form the original data.
Division into packets, transmission and reassembly is governed by a transmission protocol.
Packet Aggregation
Packet aggregation means combining packets into larger units, in order to reduce the overhead associated with each transmission.
Packet Loss
When packets are transmitted in a network they may travel different routes from source to destination. This means there is no guarantee that packets will arrive in time or arrive at all. They may also be denied at the receiver due to a full buffer or other issues. A collective term this is packet loss.
Packet Scheduler / Queueing Discipline
A queueing discipline / packet scheduler is a network function that distributes available bandwidth to different connections according to an algorithm.
The management is done by deciding how many packets each connection is handed, by handling the device traffic queue and making prioritizing incoming/ingress or outgoing/egress packets.
The scheduling can be done either by automatically, based on observed traffic, or following rules according to a Quality Of Service protocol such as Intserv or DiffServ.
Pairing
Pairing is the process of making two compatible wireless devices able to communicate with each other. This is normally done by making them visible to each other, and providing a PIN code for identification.
PAP
Password Authentication Protocol (CHAP) is a method used to authenticate PPP sessions.
PAP works like a standard login procedure; using a static user name and password combination.
PBX
A Private Branch Exchange (PBX) is a switch used for connecting telephone devices or virtual applications in an organization. It manages internal communication in the network and provides access to the external publixk switched telephone network, and allows for sharing of lines and direct communication between internal devices.
PCM
Pulse-code modulation (PCM) is the standard method for digital audio. PCM entails converting analog signals to digital values by sampling the amplitude of the analog signal at set time intervals. Each sample is quantized to the nearest value within a range of digital steps. With PCM, the ranges vary with the source amplitude, so that the steps are larger at higher amplitudes.
PCM is defined by sampling rate (number of times per second that samples are taken) and bit depth (number of different digital values).
PCR
Peak Cell Rate (PCR) defines the highest rate at which cells can be transported in an ATM connection.
PID
The PID – Process ID – is an unique idenitifer for a process, assigned to it when it is loaded into memory.
Ping
Ping is a network tool which tests accessibility of hosts on an Internet Protocol network. It measures how long a it takes for a message to travel from the measuring host to the destination and back.
PLC
Packet loss concealment (PLC) is a technique to mask the effects of packet loss in VoIP communications.
Traffic Policing
Traffic Policing is a QoS process where packets are handled according to user-defined criteria. Depending on the criteria, the packets may be marked, dropped or completely ignored.
The purpose of traffic policing is to make sure that bursts in traffic hare handled and the designated traffic flows get appropriate bandwidth.
PoP
A Point of Presence (PoP) is an access point to the Internet.
Port
A port is a communication endpoint, identified by a number, which combined with an IP address provides the necessary addressing for a service on the network.
Port Forwarding
Port forwarding is a feature that forwards inbound traffic from the internet on a specific port (or ports) to a specific device (or port) on your local network (LAN).
Port Speed
Port speed settings affect how a LAN or WAN port negotiates the speed setting.
Negotiation can be turned off (speed setting: only) or use Autonegotiation (speed setting max) to determine actual speed.
Communication on a port can be either half or full duplex.
A port that is set to disabled does not handle any traffic.
PPP
Point-to-Point Protocol (PPP) is a protocol for providing a direct data link connection with authentication, encryption and compression.
Precedence
The Precedence setting defines quality of service parameters relating to Class Selector and Assured Forwarding priority.
| ID | Setting |
|---|---|
| All | Default |
| 0 | CS1, AF11, AF12 |
| 1 | CS2, AF21, AF22 |
| 2 | CS3, AF31, AF32 |
| 3 | CS4, AF41, AF42 |
| 4 | CS5, Voice-admit, EF |
| 5 | CS5 |
| 6 | CS6 |
| 7 | CS7 |
Prefix delegation
Prefix delegation is used in DHCPv6 to assign a network address prefix and automate configuration and provisioning of the public addresses for the network.
Protocol
A protocol is a set of rules for how to handle data, specifically for transmission and management. The sender and reciever noth use the same protocol to structure, send and receive it, ensuring that the data remains intact, readable and usable.
Proxy
A proxy server works as an intermediary between the client and other servers, forwarding traffic to and from the servers and client. I adds functionality for improving aspects of the connection, such as security, reliability or simplicity.
PSDN
A packet-switched data network - PSDN - is a network where communication is done by transmitting and receiving data packets. Devices are note connected directly, but packets from different sources going to different destinations share transmission channels.
PSK
A Pre-Shared Key (PSK) is a shared secret which was previously shared between the two parties using some secure channel before it is used.
PSTN
The Public Switched Telephone Network (PSTN) is the publicly available network of telecommunication systems and services provided by telephone operators.
PTM - Pulse-Time Modulation
Pulse-Time Modulation means encoding traffic into a pulsing signal signal for transfer.
PTM Priority
The PTM Proprity defines how PTM traffic packets should be handled.
| Priority | Description |
|---|---|
| Normal Priority | Sen packets according to their priority. |
| High Priority | Use preemption; lower-priority packets are paused when higher-priority packets are sent. |
Point-to-Point Tunneling Protocol
Point-to-Point Tunneling Protocol (PTPT) is a technology for virtual private networks through TCP and a GRE with PPP packets.
Queueing Discipline / Packet Scheduler
A queueing discipline / packet scheduler is a network function that distributes available bandwidth to different connections according to an algorithm.
The management is done by deciding how many packets each connection is handed, by handling the device traffic queue and making prioritizing incoming/ingress or outgoing/egress packets.
The scheduling can be done either by automatically, based on observed traffic, or following rules according to a Quality Of Service protocol such as Intserv or DiffServ.
QoS
Quality of Service (QoS) involves setting for data traffic tha affect performance, allowing resources to be allocated depending on the needs of various types of traffic.
QoS Class
A QoS Class is a set of rules for various traffic settings that can be applied to data traffic to ensure particular needs for Quality of Service.
QoS Filter
A Quality Of Service Filter is used by classful QDiscs to determine which QoS Class a packet should belong to.
The filter contains a number of parameters/conditions that the packet needs to match in order to be enqueued in the appropriate class.
QoS Classification Group
A QoS Class group is a collection of QoS classes which can be added to an interface to provide a combination of settings.
QoS Mark
The Quality of Service Mark is used when classifying traffic. Packets matching the filter will be marked with the provided hexadecimal code 0x000000-0xFFFFFF.
This mark can then be used for identification and filtering purposes, for example by iptables .
Scheduling
Scheduling is a QoS process when a packet scheduler decides to make a packet leave earlier than other packets.
Quantization
Quantization of signals is a method where a signal is sampled at specified time intervals and the input values are approximated to provide a smaller set of values compared to the actual signal.
RADVD
The Router Advertisement Daemon - radvd is an open-source software product that provides Neighbor Discovery Protocol services.
Remote ID
The Remote ID is an identifier for the client, added to all traffic from the device itself and devices communication through it.
RFC1918
RFC 1918 - Address Allocation for Private Internets - defines standards for IP addresses in a private local network.
Addresses with in these ranges cannot be routed on the Internet:
10.0.0.0 - 10.255.255.255 (10/8 prefix) 172.16.0.0 - 172.31.255.255 (172.16/12 prefix) 192.168.0.0 - 192.168.255.255 (192.168/16 prefix)
RFC2275
RFC 2275 - View-based Access Control Model (VACM) for the Simple Network Management Protocol (SNMP)- defines an access method for resources based on view access. It limits the access of multiple users having various security levels different views of the object tree.
ROM
A Read Only Memory - ROM - is a read-only memory containing firmware for the device.
Typically, the term ROM actually refers to media that can be erased and re-programmed (is an Erasable Programmable ROM - EPROM, and Electrically Erasable Programmable ROM - EEPROM.)
Root QDisc
A Root Queueing Discipline is a Quality Of Service collection point for multiple QDiscs/packet schedulers containing classes and class groups used for QoS.
Route
The IP Route is the path a data message takes through an Internet Protocol network.
Router Advertisement
Router advertisements are NDP discovery messages periodically sent by routers from each multicast interface, announcing the IP addresses of that interface.
In NDP, Router Advertisement packets have the type 134, and can be triggered by a Router Solicitation message.
Router Solicitation
Router solicitations are NDP discovery messages used by hosts to trigger Router Advertisement messages from connected routers.
In NDP, Router Advertisement packets have the type 133.
Route metric
The route metric is used for routing decisions, and is added to routing tables to enable routing decisions.
Routing
Routing is the process of selecting paths in a network along which to send network traffic, making routing decisions to ensure that traffic moves from the source to the destination.
Dynamic routing is the most common method, where routing protocols are used to manage routing automatically.
Static routing means that routes are set up permanently using a routing table.
Policy based routing entails selecting routes based on the type of traffic being transmitted, tryingt to use more efficient routes for priority traffic.
Routing Table
A routing table is a table stored in a device used for keeping track of routes to network destinations and metrics belonging to those routes. The information in the routing table is used by devices to make routing decisions for traffic in the network.
Types of routes
| Route | Description | Comment |
|---|---|---|
| Network | Path to a specific network address. | |
| Host | Route to a specific network address by network and host ID. | Used to optimize specific types of traffic. |
| Default | Route stored in the routing table. | Used when no other routes for the destination are found. |
Request SPECification
A Request SPECification (RSPEC) is part of a Flow Specification, and defines the requirements for a flow.
Different possible service types:
| Type | Description | Examples |
|---|---|---|
| Best Effort | No guaranteed level of service. | WWW, FTP |
| Controlled Load | Behaves as Best Effort for an network without load. | |
| Guaranteed | Guarantees a minimum level of service, but no benefit wpuld be provided by higher levels. | Real-time control, latency and delay. |
| Qualitative | Not imediately quantifiable, but better than Best Effort. |
RSSI
Received signal strength indicator (RSSI) is a measurement of the power of a received radio signal.
RSS (Memory)
RSS – Resident Set Size indicatres how much memory is allocated to a process and is in RAM.
It includes all stack and heap memory, and shared libraries also in memory, but not memory that is swapped out.
RSVP
The Resource ReSerVation Protocol - RSVP - is a signalling mechanism used for network management of packets.
It uses a method where resources available to handle Quality Of Service traffic is broadcasted throughout the network.
Listening devices reply with a RESV (Reserve) message containing a flow specification for the traffic.
Devices on the route between sender and listener either accept the reservation and handle the flow, or send a reject message.
Reservations can end normally or time out as needed.
RTP
The Real-time Transport Protocol (RTP) is a protocol for handling transmission of real-time data, typically audio or video over networks services. Control and monitoring features are provided thorugh the Real Time Streaming Protocol.
RTSP
The Real Time Streaming Protocol (RTSP) is a protocol for control over transmission of real-time data with the Real-time Transport Protocol.
RXC
A RX chain is the transmit/receive signal processing hardware, such as a radio transceiver with its own antenna.
RX Chain Power Save
The RX Chain Power Save feature turns one of the receive chains off to save power.
RX Chain Power Save PPS
The maximum number of packets per second that the WLAN interface should process for during RX Chain Power Save Quiet Time before the RX Chain Power Save feature activates itself.
RX Chain Power Save Quiet Time
The number of seconds the packets per second must be below the value before the Rx Chain Power Save feature activates itself.
Samba
Samba is an open source software that provides file and print services between Linux/Unix servers and Windows-based clients.
Service Type
Service types define the guaranteed level of service in a ATM network. This involves such things as the timing between the source and destination, the guaranteed bandwidth and how many cells get lost in transmission.
| Setting | Description |
|---|---|
| UBR without PCR | Use Unspecified Bit Rate without Peak Cell Rate. |
| UBR with PCR | Use Unspecified Bit Rate with Peak Cell Rate. |
| CBR | Use Constant Bit Rate. |
| Non-Realtime VBR | Use Non-Real-Time Variable Bit Rate. |
| Realtime VBR | Use Real-Time Variable Bit Rate. |
SFP
The Small Form-factor Pluggable (SFP) connector is a hot-pluggable transceiver used for telecommunication and data.
More information:
For more information see the wikipedia article.
SIP
The Session Initiation Protocol (SIP) is a protocol for handling communication sessions, most commponly for Internet telephony for voice and video calls, as well as instant messaging, over Internet Protocol networks.
SIP Account
A SIP Account contains the identifying information and configuration for SIP communication.
SIP Address
A SIP Address is similar to a phone number for voice calls to other SIP accounts.
SIP Codec
G.711ALaw
G.711ALaw is a companding standard using non-linear encoding and decoding to provide pulse code modulation mainly of voice frequencies with the A-law variant algorithm.
G.711MuLaw
G.711MuLaw is a companding standard using non-linear encoding and decoding to provide pulse code modulation mainly of voice frequencies with the μ-law variant algorithm. It provides higher compression than A-Law, with higher distorion for smaller packets.
G.729a
G.729 is a compression standard with linear compression for voice with low bandwith rewuirements, suitable for voip applications where bandwith conservation is an issue. It divides 10ms packets for a 8kbit/s transmission rate.
G.726
SIP Domain
A SIP domain is a DNS hostname for SIP traffic routing.
SIP Realm
A SIP realm is a SIP authentication/authorization component, defining the set of usernames and passwords for a particular protection domain. The SIP realm does not have to be the same as a the SIP domain.
The SIP Realm is used together with an SIP authentication username to provide access to SIP services.
SIP Reg Interval
The SIP Reg Interval is how often connections to a SIP provider is updated. This is normally done by updating the registration with the server.
SIP Server/Registrar
A SIP server (also called SIP Registrar or SIP Proxy) handles SIP management for a IP-based private branch exchange.
It handles setup and connections for SIP calls in a network, but does not handle actual transmission of real-time data.
SIP User
A SIP User is the identifier for a SIP account. This may be a phone number.
Simple Network Management Protocol
Simple Network Management Protocol (SNMP) is a protocol for managing and devices on an IP network.
SNMP Agents
An SNMP agent provides access to managament data as variables that can be modified to perform managment tasks remotely. The variables accessible via SNMP are organized in hierarchies and stored together with metadata in Management Information Bases.
SNR - Signal to Noise Ratio
Signal-to-noise ratio (SNR) is defined as the power ratio between a signal and background noise.
It is normally measured in decibels (dB).
| dB value | Description |
|---|---|
| < 6dB | Poor. No sync, or intermittent sync problems. |
| 7dB - 10dB | Fair. Vulnerable to conditions. |
| 11dB-20dB | Good. |
| 20dB-28dB | Very good. |
| 29dB < | Excellent. |
SNR Margin
The SNR margin is the difference between the current Signal to Noise Ratio and minimal SNR required to sync at a specific transfer speed.
Higher SNR margin means a better signal, with less background noise, which in turn means a more stable the connection.
Strict Priority Precedence
Strict Priority Precedence means that where the the packets with the highest priority always are sent first.
Seamless Rate Adaptation
Seamless Rate Adaptation (SRA) allows devices to change data transfer rates on the fly to avoid losing a connection due to interference.
SRTP
The Secure Real-time Transport Protocol (SRTP) is a protocol used for providing authentication, encryption, and other se curity features with the Real-time Transport Protocol.
SRV
A Service Record (SRV record) is a specification of data in the Domain Name System containing information about IP and port for a specific service.
It is used by domain servers to keep track of their own changes without having to contact a central DNS server.
An SRV record has the form:
_Service._Proto.Name TTL Class SRV Priority Weight Port Target
| Item | Description |
|---|---|
| Service | Identifier for the service. |
| Proto | The service protocol. |
| Name | Domain name where the record is valid. |
| TTL | DNS time to live. |
| Class | DNS class (IN for Internet). |
| Priority | Target host priority, lower value means more preferred. |
| Weight | A relative weight for records with the same priority. |
| Port | Port for the service. |
| Target | Hostname for the service provider. |
SSDP
Simple Service Discovery Protocol (SSDP) is a network protocol capable of discovering universal plug and play devices on a home network.
SSH
Secure Shell (SSH) is a protocol for secure communication on networks. Most commonly it is used for remote login to devices, typically to unix shell accounts.
SSID
SSID – Service Set IDentifier, also knowns as network name, identifies a wireless network interface.
SSL
Secure Sockets Layer (SSL) is a protocol for providing security features such as authentication, privacy and data integrity in a network.
Source-Specific Multicast
Source-specific multicast (SSM) is a method of limiting delivery of multicast packets only from a requested source address.
State Code
The process state code indicates the state for a process.
| Short Code | Meaning | Description |
|---|---|---|
| D | Uninterruptible sleep | Usually refers to IO processes. |
| l | Is multi-threaded (using CLONE_THREAD, like NPTL pthreads do) | |
| L | Has pages locked into memory (for real-time and custom IO) | |
| N | Low-priority (nice to other users) | |
| R | Running runnable (on run queue) | |
| s | Is a session leader | |
| S | Interruptible sleep | Waiting for an event to complete. |
| T | Stopped | May have been stopped by control signal or trace. |
| W | Paging | Storing or retrieving data. |
| Z | Defunct (“zombie”) process | Terminated but not collected by its parent process. |
| < | High-priority | |
| + | Belongs to foreground process group. |
Static address
A static IP address is an address that doesn't change, unless manually changed by the administrator.
Static Route
A static route is a manually entered route to a network destination, which is used instead of any routes discovered automatically.
STUN
Session Traversal Utilities for NAT (STUN) consists of methods and a protocol to allow a server to discover its public IP address from behind a NAT. It is used for real-time voice, video, messaging, and other interactive IP services.
The protocol requires a STUN server located on the public side of the NAT.
Subnet Mask
A subnet mask is used to divide the IP address into network and host addresses.
Subscriber ID
A Subscriber ID is a identifier assigned to messages indepenedently from client and physical network identifiers, providing an ID that persists over network and path changes.
TCP
The Transmission Control Protocol (TCP) is a protocol to provide reliable data streams over an IP network.
TCP Flags
Transmission Control Protocol (TCP) Flags are control bits for TCP messages. These flags indicate how packets should be handled or indicate connection states.
| Flag | Description |
|---|---|
| SYN | Synchronize sequence numbers. |
| ACK | Acknowledgment field is significant. |
| FIN | No more data from sender. |
| RST | Reset the connection. |
| URG | Urgent pointer field is significant. |
| PSH | Push function. |
| CWR | Congestion Window Reduced. |
| ECE | TCP peer is ECN capable. |
TD-SCDMA
Time Division Synchronous Code Division Multiple Access (TD-SCDMA) is an UMTS 3G mobile networks in China.
TKIP
TKIP (Temporal Key Integrity Protocol) is a RC4 stream cipher is used with a 128-bit per-packet key, meaning that it dynamically generates a new key for each packet.
TLS
Transport Layer Security (TLS) is a protocol for providing security features such as authentication, privacy and data integrity in a network.
Token Bucket
A token bucket algorithm is a method of handling packet traffic, by using an analogy of a bucket containing a number of tokens that arrive at a particular rate. Tokens are used to limit when data packets are transmitted.
The depth of the bucket limits the number of tokens, and the rate of arriving tokens limits how quickly packets can be sent.
The concept is as follows:
- Tokens are added to the bucket at a fixed rate.
- If the bucket becomes full, arriving tokens are thrown away.
- Arriving data packets use up tokens from the bucket and are transmitted on the network.
This means that the bucket needs to be deep enough to handle bursts of traffic, and the token rate limits the transmission rate.
TPC
Transmission Power Control (TPC) is used to automatically adjust the transmission power level on wireless radios to avoid interference.
TPtest
TPTEST allows you to measure the speed of your Internet connection, by sending a number to and from a defined reference test server.
More information:
A list of TP test servers is available at http://tptest.sourceforge.net/servers.php.
TR069
TR-069 CPE WAN Management Protocol (CWMP) was created by the DSL Forum to standardize the Wide Area Network (WAN) management of CWMP. The TR-069 protocol specifically defines a common method for CPE devices to communicate with an Auto Configuration Server (ACS).
Traffic SPECification
A Traffic SPECification (TSPEC) is part of a Flow Specification, and describes traffic flow properties, typically involving token bucket algorithm parameters.
TTL
Time to live (TTL) is a mechanism to determine when data in a network should be discarded, for example for cache expiry, or to prevent data from being transmitted forever.
UAPSD
Unscheduled Automatic Power Save Delivery (UAPSD) is a wifi device feature which allows them to save power by dozing between transmissions.
UBIFS
UBIFS file-system stands for “Unsorted Block Images File System”.
It is a flash file system, designed to work with flash devices, using Memory Technology Device (MTD) device files.
UBUS
OpenWrt micro bus architecture - UBUS - is a combination of daemon, library and helpers to provide communication between various daemons and applications in OpenWrt.
The ubus command line tool can be used to interact with the ubusd server to and manage services through JSON .
Command referencs is available at https://wiki.openwrt.org/doc/techref/ubus.
UDP
User Datagram Protocol (UDP) is a protocol to provide relatively unreliable data streams over an IP network. It provides no guarantees for delivery and no protection from duplication.
The simplicity of UDP reduces the overhead from using the protocol and the services may be adequate in many cases.
UMTS
Universal Mobile Telecommunications System (UMTS) is a third generation mobile cellular system for networks based on the GSM standard.
Unicast
Unicast is communication where information is addressed to a single destination.
Unmanaged
The interface protocol type Unmanaged means that the connection has no defined protocol.
Uplink
An uplink interface type is an interface to services.
UPnP
Universal Plug and Play (UPnP) is a set of networking protocols used for automatic discovery and communication on a network. It makes it possible for various devices to connect and share services.
UPnP involves automatic port forwarding set up without user interaction. This may constitute a security risk.
USB
USB – Universal Serial Bus is a standard for connection, communication, and power supply between computers and electronic devices.
User Class
The User Class uniquely identifies the type or category of user or applications it represents.
UUID
A Universally Unique Identifier (UUID) is an 128-bit identifier used to uniquely identify objects.
Example: 65613210-44d4-11e6-beb8-9e71128cae77
VBR
The service type Variable Bit Rate come in two variants: Non-Realtime VBR and Realtime VBR.
Non-Realtime VBR
Non-Real-Time Variable Bit Rate (nrt-VBR) is used for connections that need guaranteed bandwidth or latency, but do not rely on accurate timing between source and destination.
Realtime VBR
Real-Time Variable Bit Rate (rt-VBR) is used for connections that need accurate timing between source and destination.
VCI
Virtual Channel Identifier - VCI, is used together with VPIs to enable ATM networks.
In an ATM network, each circuit is given a virtual channel identifier, and and each path is given a virtual path identifier.
The VCI identifies circuit/channel in use, and VPI matches the appropriate path to the desired destination host.
Vendor ID
A Vendor ID - VID - is a unique number identifying a device.
Virtual Network Interface
Virtual network interfaces are linked to a hardware device, but are not hardware devices.
A virtual network interface is generally associated with a physical network, another virtual interface, a loopback interface or other standalone interfaces.
Types of Virtual Network Interfaces
| Type | Example | Description |
|---|---|---|
| Aliases | eth4:5, eth4:6 | Used to handle multiple IP-addresses per interface. Supported for backwards compatibility. |
| Bridges | br0, br-lan | Used to make multiple network interfaces behave as one network interface. |
| Stacked VLANs | 10, 20 | IEEE 802.1ad type network, using two or more tags in each packet. |
| Special purpose | imq0, teql3 | Used to change the order of outgoing or incoming network packets. |
| Tunnel interfaces | pppoe-dsl, tun0, vpn1 | Used to send packets over a tunneling protocol. |
| VLANs | eth4.0, vlan0 | Used to separate a network into multiple virtual networks. |
| Wireless operating mode virtual interfaces | wlan0, ath3 | A wireless subsystem created automatically for a wireless NIC master interface. |
VLAN
A virtual LAN (VLAN) is, as the name implies, a virtualized LAN. Most commonly a VLAN is a subdivision of a network.
VLANs also allow grouping of hosts together even if the hosts are not connected to the same network device, and managing them through software.
VOIP
VoIP - Voice Over IP is a group of technologies for the delivery of voice communications and multimedia sessions over Internet Protocol networks.
VPI
A Virtual Path Identifier - VPI, is used together with VCIs to enable ATM networks.
In an ATM network, each circuit is given a virtual channel identifier, and and each path is given a virtual path identifier.
The VCI identifies circuit/channel in use, and VPI matches the appropriate path to the desired destination host.
VPN
A virtual private network (VPN) is a secured, private network connected through a public network.
VSZ
VSZ is the Virtual Memory Size. It includes all memory that the process can access, including memory that is swapped out and memory that is from shared libraries.
%VSZ
VSZ is the Virtual Memory Size. It includes all memory that the process can access, including memory that is swapped out and memory that is from shared libraries.
WAN
A Wide Area Network (WAN) is network that extends over a large geographical distance.
WCDMA
Wideband Code Division Multiple Access (W-CDMA) is a mobile communications technology using CDMA for broadband.
WEP
Wired Equivalent Privacy (WEP) is a security algorithm intended to provide security comparable a wired network.
WEP uses a key of 10 or 26 hexadecimal digits.
Weighted Fair Queuing
Weighted Fair Queuing means that bandwidth is adjusted automatically according to traffic priority and weight value.
WiFi
WiFi or Wi-Fi is a technology allowing devices to connect to a wireless LAN (WLAN) network. The term “Wi-Fi” is a play on words relating to hi-fi (high fidelity) from the music industry. Communication is commonly done over 2.4 gigahertz and 5 gigahertz radio bands.
WiFi band
A wifi band is a collection of wifi channels provided by a particular wifi radio.
Bands are identified by their frequency as measured in Gigahertz (GHz).
Standard bands are 2.4GHz and 5Ghz.
WiFi channel
A wifi channel is a frequency range in a specific wifi band used for wifi communication.
WiFi encryption
WiFi encryption means to encrypt the messages that are sent between nodes on a wireless network.
A wifi interface can use one of several encryption options:
| None | No encryption. |
| WEP | Wired Equivalent Privacy |
| WPA2 Personal (PSK) | Wi-Fi Protected Access |
| WPA/WPA2 Personal (PSK) Mixed Mode | Wi-Fi Protected Access II Pre-Shared Key |
| WPA2 Enterprise | Wi-Fi Protected Access II Enterprise |
| WPA/WPA2 Enterprise Mixed Mode | Wi-Fi Protected Access Enterprise / Wi-Fi Protected Access II Enterprise |
WiFi interface
A wireless interface is the access point to a wireless radio. Interfaces are identified by their SSID.
Each radio can have several SSIDs and each SSID interface can be configured as part of a network bridge or firewall group.
WiFi Key
The WiFI Key or passphrase is a shared secret between client and server used for encryption and decryption in wireless networks.
WiFi Mode
The WiFi Mode defines which to use for wireless communication in the network.
Auto
The Auto Mode allows the device to automatically select a suitable profile among the available options.
802.11a
802.11a is a wireless radio specification for the 5 GHz band with a maximum data rate of 54 Mbit/s.
802.11ac
802.11ac is a wireless radio specification for both the 2.4 GHz and the 5 GHz bands with support for multiple-input multiple-output antennas, providing a maximum data rate from 433 Mbit/s to 1300 Mbit/s.
802.11b
802.11b is a wireless radio specification for the 2.4GHz band with a maximum data rate of 11 Mbit/s .
802.11b/g
802.11b/g is a wireless radio specification combining 802.11b and 802.11g standards in dual band mode.
802.11g
802.11g is a wireless radio specification for the 2.4 GHz band with a maximum data rate of 54 Mbit/s.
802.11n
802.11n is a wireless radio specification for both the 2.4 GHz and the 5 GHz bands with support for multiple-input multiple-output antennas, providing a maximum data rate from 54 Mbit/s to 600 Mbit/s.
Wireless radio
A wireless radio is the device sending out a wireless signal. Each radio can have several interfaces associated with it.
LAN
A Wireless Local Area Network is Local Area Network connected through one or several access points.
WMM / WME
WiFi Multimedia - WMM (also known as WiFi Multimedia Extension - WME) - improves quality of service on a network by prioritizing data by four configurable categories:
Voice: Voice packets for Voice over IP (VoIP) calls.
Video: Video packets for support of TV streams.
Best effort: Support for legacy devices or devices lacking QoS standards.
Background: File downloads, print jobs and other traffic that does not suffer from increased latency.
WMM does not provide guaranteed throughput.
WMM Acknowledgement
WMM (WiFi Multimedia) Acknowledgement is a verification signal sent from the client to the device to indicate that no error has been detected for the data .
WMM Power Save
WMM Power Save allows small devices, such as phones and PDAs, to transmit data while in a low-power status.
WPA2 Enterprise
Wi-Fi Protected Access 2 Enterprise is designed for enterprise networks and requires an authentication server.
It provides additional security (e.g. protection against dictionary attacks on short passwords).
Various kinds of the Extensible Authentication Protocol (EAP) are used for authentication.
WPA2 PSK
Short for Wi-Fi Protected Access 2 – Pre-Shared Key, and also called WPA2 Personal, it is a method of securing your network using Pre-Shared Key (PSK) authentication,
Wi-Fi Protected Access 2 Personal uses pre-shared passphrases between 8 and 63 characters long.
The wireless device converts the preshared key to a hash and uses that for communication authentication.
WPA Enterprise
Also referred to as WPA-802.1X mode, and sometimes just WPA (as opposed to WPA-PSK), is designed for enterprise networks and requires an authentication server.
It provides additional security (e.g. protection against dictionary attacks on short passwords).
Various kinds of the Extensible Authentication Protocol (EAP) are used for authentication.
WPA personal
Wi-Fi Protected Access (WPA), also referred to as WPA-PSK (pre-shared key) does not require an authentication server.
It uses TKIP, with a key either as a string of 64 hexadecimal digits, or as a passphrase of 8 to 63 characters.
WPA also includes a message integrity check, which is designed to prevent an attacker from altering and resending data packets.
WPA-Personal mode is available with both WPA and WPA2.
WPS
Wi-Fi Protected Setup (WPS) is an authentication key distribution method. It can be performed in one of several ways.
PIN code: A PIN is entered on the client.
Push button: An actual or virtual button is pressed on the device and the client within a short amount of time.
Near field: The client is brought physically close to the device.
USB: An USB device is used to transfer data between the new client and the device. (Deprecated)
WWAN
A Wireless Wide Area Network (WWAN), is a wireless network that extends over a large geographical distance.
2G
Second-generation wireless telephone technology (2G), is a cellular network for digital mobile data communication.
3G
Third-generation wireless telephone technology (3G), is a cellular network for digital mobile data communication for broadband traffic.
4G
Fourth-generation wireless telephone technology (4G), is a cellular network for digital mobile data communication for high-speed broadband.
802.1p
802.1p is a standard for priority levels, identifying the class of service a VLAN is to be used for. There are 8 different levels, numbered from 0 to 7.
| Priority | Acronym | Traffic types | Comment |
|---|---|---|---|
| 0 | BK | Background | Lowest |
| 1 | BE | Best Effort | |
| 2 | EE | Excellent Effort | |
| 3 | CA | Critical Applications | |
| 4 | VI | Video | < 100 ms latency and jitter |
| 5 | VO | Voice | < 10 ms latency and jitter |
| 6 | IC | Internetwork Control | |
| 7 | NC | Network Control | Highest |
802.1q
IEEE 802.1Q is a standard for Ethernet VLANs where VLANs are given a numeric tag. The tag is used to identify traffic in networks, and decide how to handle it.
This allows multiple bridged networks to share the same physical link without leaking information to each other networks.
802.11a
802.11a is a wireless radio specification for the 5 GHz band with a maximum data rate of 54 Mbit/s.
802.11ac
802.11ac is a wireless radio specification for both the 2.4 GHz and the 5 GHz bands with support for multiple-input multiple-output antennas, providing a maximum data rate from 433 Mbit/s to 1300 Mbit/s.
802.11b
802.11b is a wireless radio specification for the 2.4GHz band with a maximum data rate of 11 Mbit/s .
802.11b/g
802.11b/g is a wireless radio specification combining 802.11b and 802.11g standards in dual band mode.
802.11g
802.11g is a wireless radio specification for the 2.4 GHz band with a maximum data rate of 54 Mbit/s.
802.11n
802.11n is a wireless radio specification for both the 2.4 GHz and the 5 GHz bands with support for multiple-input multiple-output antennas, providing a maximum data rate from 54 Mbit/s to 600 Mbit/s.